Cybercriminal Makes Millions From Executive Office365 Account Breaches
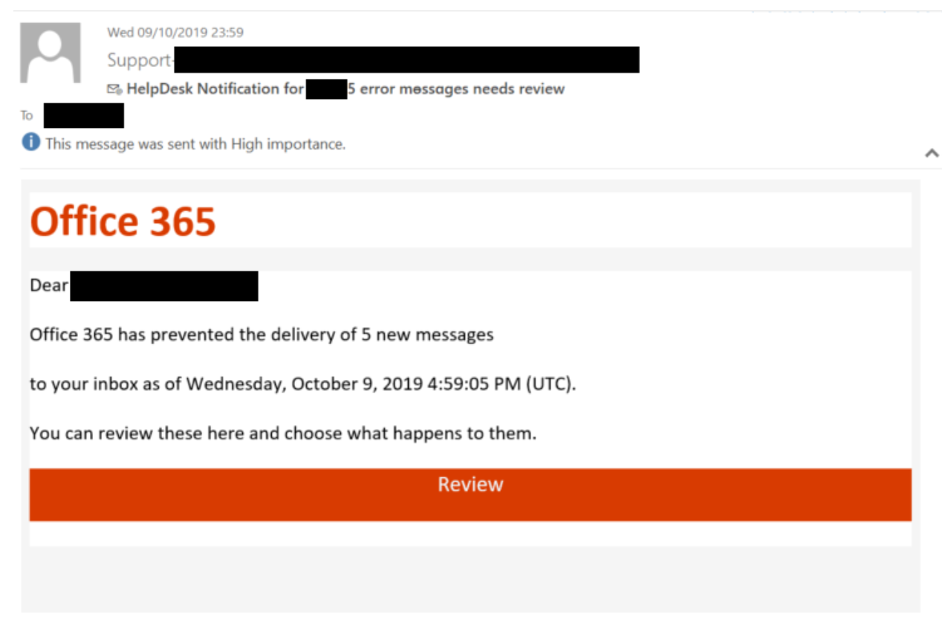
Table of Contents
Methods Employed by the Cybercriminal
Cybercriminals utilize a range of sophisticated techniques to breach Executive Office365 accounts. Their success hinges on exploiting human vulnerabilities and leveraging technical weaknesses.
Phishing and Spear Phishing Attacks
Phishing and spear-phishing emails are highly effective tools in the cybercriminal's arsenal. These attacks often involve:
- Deceptive Links: Emails containing malicious links disguised as legitimate website addresses, leading to phishing websites designed to steal credentials.
- Malicious Attachments: Emails with attachments containing malware, such as keyloggers or ransomware, that infect the victim's system upon opening.
- Impersonation: Cybercriminals impersonate trusted individuals, such as CEOs, CFOs, or IT support staff, to gain the victim's trust and manipulate them into divulging sensitive information or clicking malicious links. For example, an email seemingly from the CEO requesting urgent financial information is a common tactic.
These attacks are often highly targeted, utilizing publicly available information about executives and their companies to craft believable and persuasive emails. The more personalized the email, the higher the chance of success.
Credential Stuffing and Brute-Force Attacks
Cybercriminals also employ automated attacks to gain access to Executive Office365 accounts. These include:
- Credential Stuffing: This technique uses stolen credentials from data breaches on other platforms to attempt logins on Office365. If an executive reuses passwords, their Office365 account becomes vulnerable.
- Brute-Force Attacks: These attacks involve systematically trying various password combinations until the correct one is found. Weak passwords, easily guessed passwords or passwords reused across multiple platforms are particularly susceptible.
These automated attacks can be incredibly effective, especially against accounts with weak or easily guessed passwords. Therefore, using strong, unique passwords for each account is crucial.
Exploiting Software Vulnerabilities
Outdated software and unpatched systems represent significant vulnerabilities that cybercriminals actively exploit. This includes:
- Unpatched Systems: Failing to update software leaves systems susceptible to known vulnerabilities, allowing attackers to gain unauthorized access.
- Outdated Software: Using outdated versions of software means missing out on critical security updates and patches, creating entry points for cybercriminals.
Regular software updates and prompt application of security patches are essential to mitigate these risks and prevent successful breaches.
Financial Impact of Executive Office365 Account Breaches
The financial consequences of successful Executive Office365 account breaches can be catastrophic.
Data Theft and Extortion
Compromised accounts provide access to sensitive company data, including:
- Confidential Business Information: Trade secrets, strategic plans, and financial data can all be stolen and sold on the dark web.
- Customer Data: Personal information of customers, including names, addresses, and financial details, can be misused for identity theft or sold to other cybercriminals.
- Regulatory Fines: Data breaches often lead to significant regulatory fines and penalties, adding substantially to the overall financial burden. The reputational damage caused can also be long-lasting and costly.
Financial Fraud and Embezzlement
Cybercriminals can use compromised accounts to:
- Initiate fraudulent transactions: They can transfer funds, issue invoices, or make payments without authorization, causing significant financial losses.
- Manipulate financial records: They can alter financial records to conceal their activities or embezzle funds.
The financial impact of such fraudulent activities can be devastating, potentially leading to bankruptcy for smaller organizations.
Lost Productivity and Business Disruption
Breaches also lead to:
- Disruption of business operations: Access to critical systems and data may be lost or compromised, halting operations until the situation is resolved.
- Costs of investigation and recovery: Investigating a breach, recovering lost data, and implementing new security measures can be exceptionally expensive.
- Loss of productivity: Employees may be unable to work effectively while the breach is being addressed.
The long-term consequences of these disruptions can significantly impact a company's profitability and competitiveness.
Protecting Against Executive Office365 Account Breaches
Protecting against Executive Office365 account breaches requires a multi-layered approach focusing on technical and human elements.
Multi-Factor Authentication (MFA)
Implementing MFA is critical to enhance account security. MFA adds an extra layer of security by requiring more than just a username and password to access an account. This could include:
- One-Time Passwords (OTP): These are generated by an app or sent via text message.
- Biometric Authentication: Using fingerprints or facial recognition for authentication.
MFA significantly reduces the risk of unauthorized access, even if credentials are compromised.
Security Awareness Training
Regular security awareness training is essential, particularly for executives:
- Phishing Email Recognition: Training employees to identify and report suspicious emails.
- Password Security Best Practices: Emphasizing the importance of strong, unique passwords and promoting secure password management practices.
- Cybersecurity Best Practices: Educating employees about general cybersecurity risks and best practices.
Cultivating a security-conscious culture within the organization significantly reduces the likelihood of successful phishing attacks.
Robust Password Policies and Management
Strong password policies are essential:
- Password Complexity: Enforcing strong password requirements, including minimum length, character types, and regular changes.
- Password Managers: Encourage the use of password managers to securely store and manage complex passwords.
By combining these measures, companies can effectively strengthen their defenses against cyberattacks.
Conclusion: Safeguarding Your Business from Executive Office365 Account Breaches
Cybercriminals are employing increasingly sophisticated methods to breach Executive Office365 accounts, leading to significant financial and reputational risks. The methods explored, from phishing attacks to exploiting software vulnerabilities, highlight the need for a proactive and multi-faceted security approach. Implementing robust security measures, including MFA, regular security awareness training, and strong password policies, is crucial to protect your business from the devastating consequences of Executive Office365 Account Breaches. Protect your business today!

Featured Posts
-
 Dakota Johnson Family And Materialist Cast At La Screening
May 09, 2025
Dakota Johnson Family And Materialist Cast At La Screening
May 09, 2025 -
 Rakesh Sharma From Space To Present Day A Look At His Career
May 09, 2025
Rakesh Sharma From Space To Present Day A Look At His Career
May 09, 2025 -
 Alpine Bosss Stern Warning To Doohan Latest F1 News
May 09, 2025
Alpine Bosss Stern Warning To Doohan Latest F1 News
May 09, 2025 -
 Bitcoin Seoul 2025 Networking And Innovation In Asia
May 09, 2025
Bitcoin Seoul 2025 Networking And Innovation In Asia
May 09, 2025 -
 Edmonton Unlimiteds New Strategy Scaling Tech Innovation For Global Impact
May 09, 2025
Edmonton Unlimiteds New Strategy Scaling Tech Innovation For Global Impact
May 09, 2025
Latest Posts
-
 Is A 40 Increase In Palantir Stock By 2025 Realistic
May 09, 2025
Is A 40 Increase In Palantir Stock By 2025 Realistic
May 09, 2025 -
 Palantir Stock Prediction 2025 Should You Invest Now
May 09, 2025
Palantir Stock Prediction 2025 Should You Invest Now
May 09, 2025 -
 Stock Market Today Sensex Nifty Updates And Analysis
May 09, 2025
Stock Market Today Sensex Nifty Updates And Analysis
May 09, 2025 -
 Investing In Palantir Stock Before May 5th A Comprehensive Guide
May 09, 2025
Investing In Palantir Stock Before May 5th A Comprehensive Guide
May 09, 2025 -
 Sensex Live 100 Points Higher Nifty Above 17 950 Market Analysis
May 09, 2025
Sensex Live 100 Points Higher Nifty Above 17 950 Market Analysis
May 09, 2025
