Cybercriminal Nets Millions From Executive Office365 Account Breaches
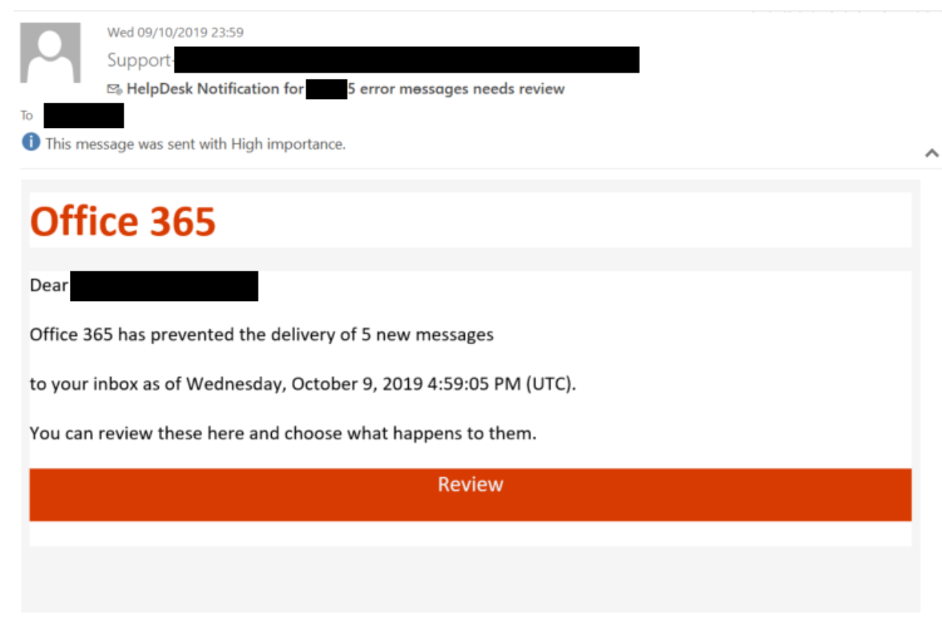
Table of Contents
The Methods Behind Executive Office365 Account Breaches
Cybercriminals employ various tactics to gain unauthorized access to executive Office 365 accounts. Understanding these methods is the first step towards effective prevention.
Phishing and Spear Phishing Attacks
Phishing and spear phishing are prevalent attack vectors. Sophisticated phishing emails, often disguised as legitimate communications, lure unsuspecting executives into revealing their credentials or downloading malware.
- Lures: These emails frequently mimic urgent payment requests, fake invoices from trusted vendors, or notifications from seemingly official sources.
- Technical Methods: Attackers often use techniques like URL spoofing to redirect victims to fake login pages that capture their credentials. Malicious attachments containing macros or other exploits are also commonly used.
- Example: An email might appear to be from a senior executive requesting an urgent wire transfer, using official company letterhead and branding to add legitimacy.
Credential Stuffing and Brute-Force Attacks
Cybercriminals also utilize stolen credentials obtained from other platforms (data breaches on other sites) to attempt access to Office 365 accounts. This technique, known as credential stuffing, leverages leaked usernames and passwords from previous breaches.
- Credential Stuffing: Attackers use automated tools to test stolen credentials against various platforms, including Office 365.
- Brute-Force Attacks: These attacks involve systematically trying various password combinations until the correct one is found. Weak passwords are particularly vulnerable.
- Mitigation: The importance of strong, unique passwords and multi-factor authentication (MFA) cannot be overstated. MFA adds an extra layer of security, making it significantly harder for attackers to gain access even if they possess the username and password.
Exploiting Software Vulnerabilities
Attackers may exploit known vulnerabilities in Office 365 or related software to gain unauthorized access. Outdated software is a prime target for exploitation.
- Software Updates: Regular software updates and patching are crucial to mitigating the risk of vulnerabilities being exploited.
- Vulnerability Scanning: Regular vulnerability scanning and penetration testing identify potential weaknesses in an organization's security posture.
- Zero-Day Exploits: The risk of zero-day exploits (newly discovered vulnerabilities) highlights the need for proactive security measures.
The Financial Ramifications of Executive Office365 Account Breaches
The financial consequences of executive Office365 account breaches can be devastating, extending far beyond the direct financial losses.
Direct Financial Losses
Compromised executive accounts often lead to significant direct financial losses:
- Fraudulent Wire Transfers: Attackers can initiate fraudulent wire transfers, diverting funds to their own accounts.
- Data Theft: Sensitive financial data, intellectual property, and customer information are at risk of being stolen and sold on the dark web.
- Real-World Examples: Numerous cases demonstrate the potential for millions of dollars in losses due to successful attacks targeting executive accounts.
Reputational Damage and Legal Costs
Beyond the direct financial impact, breaches cause significant reputational damage:
- Loss of Trust: Customers and partners lose trust in an organization that has suffered a data breach.
- Legal Action: Organizations may face legal action from affected individuals, regulatory bodies, and shareholders.
- Regulatory Fines: Regulatory fines and penalties can further amplify the financial burden.
Best Practices to Prevent Executive Office365 Account Breaches
Proactive measures are essential to protect against executive Office365 account breaches.
Implementing Robust Security Measures
Robust security measures are crucial for mitigating risk:
- Multi-Factor Authentication (MFA): Implement MFA for all accounts, especially executive accounts.
- Security Awareness Training: Regular security awareness training for all employees, particularly executives, is essential to educate them about phishing and other threats.
- Strong Password Policies: Enforce strong password policies and encourage the use of password management tools.
Leveraging Advanced Security Technologies
Advanced security technologies enhance protection:
- Advanced Threat Protection: Utilize advanced threat protection tools to detect and prevent sophisticated attacks.
- Email Security Solutions: Implement email security solutions capable of detecting and blocking malicious emails and attachments.
- Regular Security Audits: Conduct regular security audits and vulnerability assessments to identify and address potential weaknesses.
Conclusion
Executive Office365 account breaches pose a significant and growing threat to businesses worldwide. The financial and reputational consequences can be catastrophic. By implementing robust security measures, leveraging advanced security technologies, and educating employees, organizations can significantly reduce their risk of becoming victims. Don't become another statistic. Protect your executive Office365 accounts and your bottom line by implementing the security best practices discussed in this article. Learn more about securing your Office365 environment today!

Featured Posts
-
 2000 Yankees Diary Joe Torres Meetings And Andy Pettittes Shutout Of The Twins
Apr 28, 2025
2000 Yankees Diary Joe Torres Meetings And Andy Pettittes Shutout Of The Twins
Apr 28, 2025 -
 Understanding The Recent Surge In Gpu Costs
Apr 28, 2025
Understanding The Recent Surge In Gpu Costs
Apr 28, 2025 -
 2000 Yankees Diary Bombers Defeat Royals In Thrilling Victory
Apr 28, 2025
2000 Yankees Diary Bombers Defeat Royals In Thrilling Victory
Apr 28, 2025 -
 Silent Treatment And Divorce Recognizing The Patterns
Apr 28, 2025
Silent Treatment And Divorce Recognizing The Patterns
Apr 28, 2025 -
 Perplexitys Ceo On The Ai Browser War Taking On Google
Apr 28, 2025
Perplexitys Ceo On The Ai Browser War Taking On Google
Apr 28, 2025
Latest Posts
-
 Predicting A Jarren Duran Esque Breakout This Red Sox Outfielder To Watch
Apr 28, 2025
Predicting A Jarren Duran Esque Breakout This Red Sox Outfielder To Watch
Apr 28, 2025 -
 The End Of An Era Orioles Hit Streak And The Announcer Jinx
Apr 28, 2025
The End Of An Era Orioles Hit Streak And The Announcer Jinx
Apr 28, 2025 -
 160 Game Hit Streak Snapped The Orioles Broadcaster Jinx
Apr 28, 2025
160 Game Hit Streak Snapped The Orioles Broadcaster Jinx
Apr 28, 2025 -
 Orioles Announcers Curse Lifted After 160 Game Hit Streak
Apr 28, 2025
Orioles Announcers Curse Lifted After 160 Game Hit Streak
Apr 28, 2025 -
 Orioles Broadcasters Jinx Broken 160 Game Hit Streak Ends
Apr 28, 2025
Orioles Broadcasters Jinx Broken 160 Game Hit Streak Ends
Apr 28, 2025
