Cybercriminal's Office365 Scheme Nets Millions, FBI Alleges
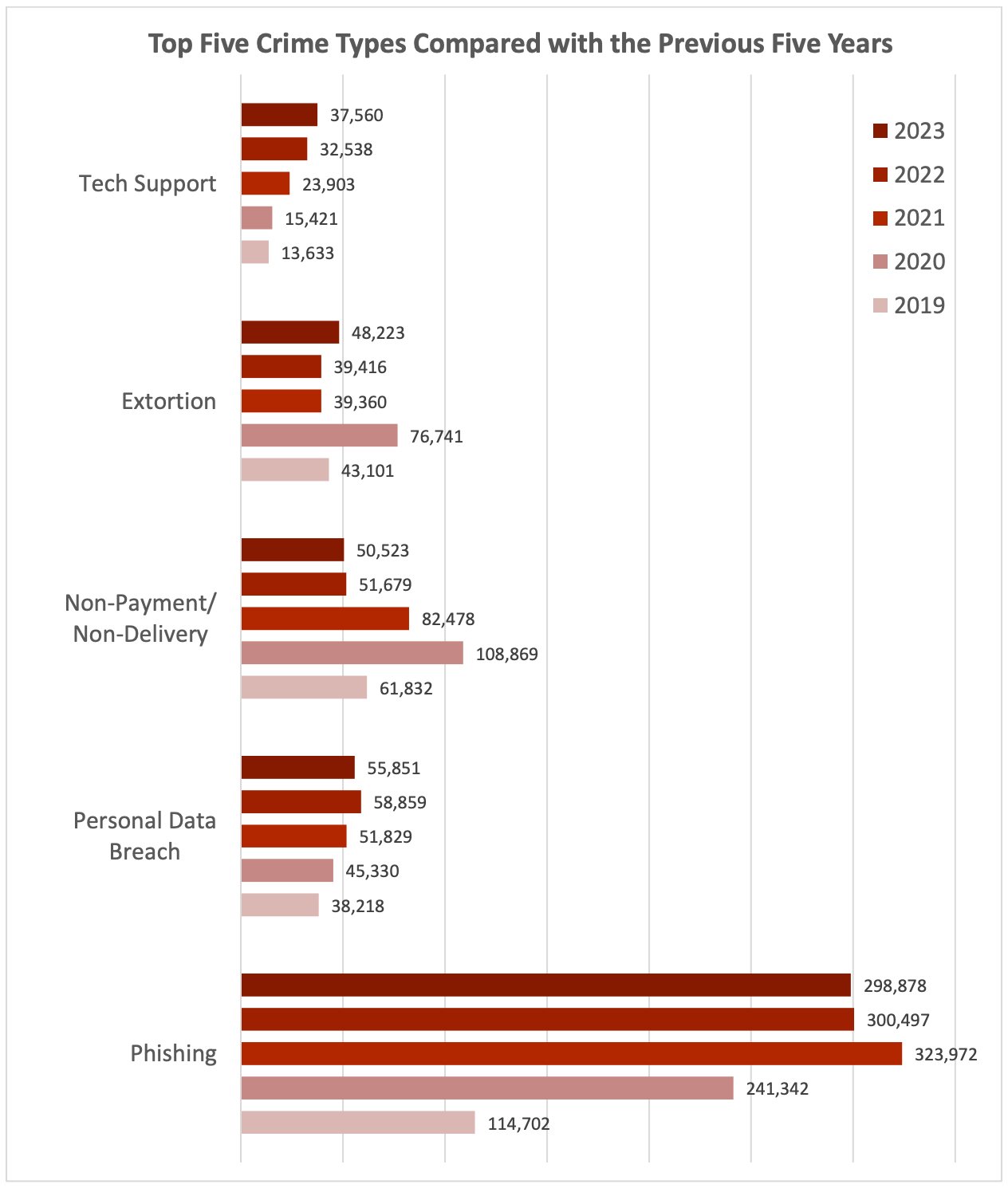
Table of Contents
Understanding the Office365 Cybercriminal Tactics
Cybercriminals are employing increasingly sophisticated methods to exploit vulnerabilities within the Office365 ecosystem. Their goal is simple: access sensitive data and financial accounts for personal gain. The Office365 security breach often starts with seemingly innocuous attacks, quickly escalating into significant damage. Here are some of the key tactics:
- Phishing attacks targeting Office365 login credentials: These attacks often use convincing emails mimicking legitimate communications, urging recipients to click malicious links or enter their login details on fake login pages. This is a common vector for Office365 security breaches.
- Exploiting weak passwords and MFA bypass techniques: Many users still rely on weak, easily guessable passwords. Cybercriminals actively seek these weaknesses, often combining them with sophisticated techniques to bypass multi-factor authentication (MFA) security.
- Using compromised accounts to access sensitive data: Once an account is compromised, cybercriminals can access emails, files, and other sensitive data, potentially leading to identity theft, financial fraud, or intellectual property theft. This demonstrates a significant Office365 security vulnerability.
- Malware deployment via malicious attachments or links: Malicious attachments or links hidden within seemingly harmless emails can install malware on victims' computers, enabling further access and control over the compromised account and network. This often leads to a widespread malware infection.
- Account takeover leading to data breaches and financial fraud: The ultimate goal is often account takeover. Once control is gained, the criminals can initiate fraudulent transactions, steal sensitive information, or launch further attacks against other accounts. This constitutes a serious Office365 security breach and data theft.
The FBI's allegations provide specific examples of these tactics, illustrating how seemingly small security oversights can lead to significant financial and reputational damage.
The Scale of the Office365 Cybercrime Ring and its Impact
The FBI's investigation reveals a staggering scale to this Office365 cybercrime scheme. The financial losses alleged run into millions of dollars, impacting a significant number of victims. The scheme targeted a wide range of organizations, including:
- Total financial losses reported by the FBI: While exact figures may not be publicly released for investigative reasons, the scale of the losses is substantial.
- Number of victims or compromised accounts: The number of victims affected is likely far greater than initially reported, indicating a widespread impact.
- Industries most heavily impacted: The FBI's investigation likely reveals patterns targeting specific industries particularly vulnerable to these types of attacks (e.g., finance, healthcare, government).
- Reputational damage and loss of customer trust: Beyond financial losses, the reputational damage caused by a data breach can be devastating, leading to loss of customer trust and long-term business consequences.
These statistics paint a clear picture of the serious threat posed by this Office365 cybercrime scheme, emphasizing the need for robust cybersecurity measures.
Preventing Office365 Cybercrime: Best Practices and Security Measures
Protecting yourself and your organization from similar attacks requires a multi-layered approach to Office365 security. These measures should be integrated into your overall cybersecurity strategy:
- Strong password policies and multi-factor authentication (MFA): Enforce strong password policies and mandatory multi-factor authentication to significantly reduce the risk of unauthorized access. This is a crucial element of MFA security.
- Regular security awareness training for employees: Educate employees about phishing scams, malware threats, and other common social engineering tactics. Regular cybersecurity awareness training is vital.
- Implementing robust email security solutions (spam filters, anti-phishing tools): Utilize advanced email security solutions to filter out malicious emails and prevent phishing attempts. This involves robust email security.
- Regular software updates and patching: Keep your software and operating systems up-to-date with the latest security patches to mitigate known vulnerabilities. This is essential for Office365 security.
- Data backup and recovery plans: Implement robust data backup and recovery plans to minimize data loss in the event of a successful attack.
- Incident response planning: Develop and regularly test your incident response plan to ensure you're prepared to handle a security breach effectively.
The FBI's Investigation and Legal Ramifications
The FBI's investigation into this Office365 cybercrime scheme is ongoing. The legal ramifications for the perpetrators are significant, potentially including:
- Details about the FBI's investigation timeline: The investigation likely involves extensive digital forensics and collaboration with international law enforcement agencies.
- Potential charges against the perpetrators: Perpetrators could face a range of charges, including wire fraud, identity theft, and computer crimes.
- Status of any ongoing legal proceedings: The legal process can be lengthy, with potential for significant penalties including hefty fines and imprisonment.
Conclusion: Safeguarding Your Business from Office365 Cybercrime
The Office365 cybercrime scheme highlighted by the FBI underscores the critical need for robust cybersecurity practices. The financial and reputational risks associated with these attacks are substantial. Don't become the next victim. Implement strong Office365 security practices today! This includes enforcing strong passwords, enabling multi-factor authentication, providing regular security awareness training to your employees, and investing in advanced email security solutions. Proactive measures to prevent Office365 breaches are vital for protecting your data and your business's future. Take immediate steps to improve your Office365 security and protect yourself from the devastating consequences of cybercrime.

Featured Posts
-
 India Pakistan Relations Understanding The Kashmir Dispute And The Risk Of Conflict
May 08, 2025
India Pakistan Relations Understanding The Kashmir Dispute And The Risk Of Conflict
May 08, 2025 -
 Chinas Automotive Market Opportunities And Obstacles For Premium Brands Like Bmw And Porsche
May 08, 2025
Chinas Automotive Market Opportunities And Obstacles For Premium Brands Like Bmw And Porsche
May 08, 2025 -
 El Betis Una Historia Forjada En Verde
May 08, 2025
El Betis Una Historia Forjada En Verde
May 08, 2025 -
 Is War Imminent Analyzing The India Pakistan Standoff Over Kashmir
May 08, 2025
Is War Imminent Analyzing The India Pakistan Standoff Over Kashmir
May 08, 2025 -
 Dissecting The Thunder And Bulls Offseason Trade A Deeper Dive
May 08, 2025
Dissecting The Thunder And Bulls Offseason Trade A Deeper Dive
May 08, 2025
Latest Posts
-
 Hunger Games Directors New Film Dystopian Horror Trailer Unveiled
May 08, 2025
Hunger Games Directors New Film Dystopian Horror Trailer Unveiled
May 08, 2025 -
 New Horror Movie Trailer Dystopian Games Based On Underrated Stephen King Novel
May 08, 2025
New Horror Movie Trailer Dystopian Games Based On Underrated Stephen King Novel
May 08, 2025 -
 Stephen King Adaptation The Contest From Hell Trailer Released
May 08, 2025
Stephen King Adaptation The Contest From Hell Trailer Released
May 08, 2025 -
 The Long Walk Movie Stephen Kings Classic Coming To The Big Screen
May 08, 2025
The Long Walk Movie Stephen Kings Classic Coming To The Big Screen
May 08, 2025 -
 Stephen Kings The Long Walk Movie Adaptation Finally A Reality
May 08, 2025
Stephen Kings The Long Walk Movie Adaptation Finally A Reality
May 08, 2025
