Data Breach: 90+ NHS Employees Viewed Nottingham Attack Victim Files
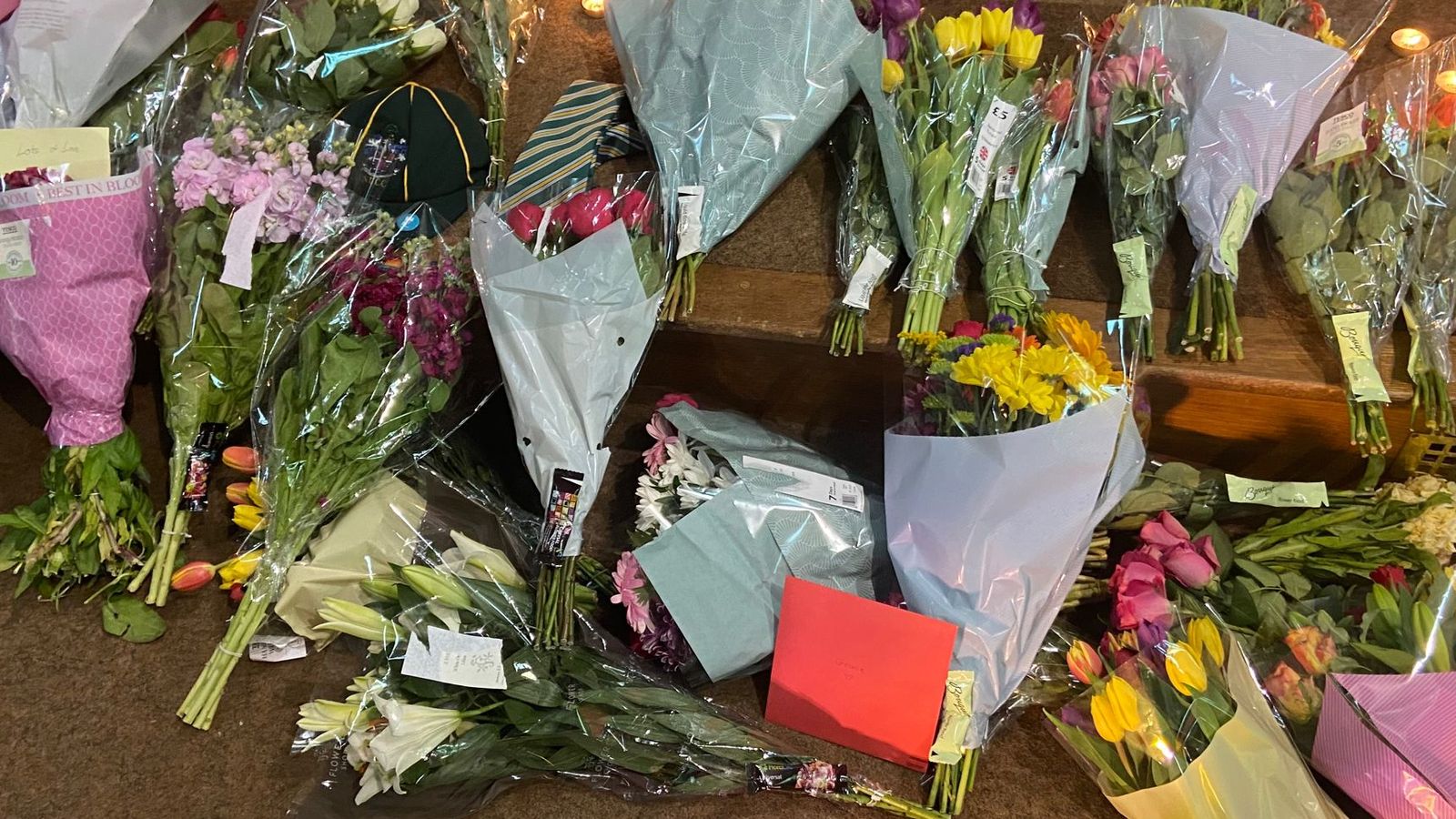
Table of Contents
The Scale of the Data Breach: 90+ NHS Employees Accessed Sensitive Information
The sheer number of NHS employees involved – over 90 – underscores the gravity of this NHS data breach. These employees, spanning various roles within the healthcare system, accessed sensitive information belonging to victims of the tragic Nottingham attack. The precise nature of their roles is still under investigation, but it's clear that a significant breach of trust occurred.
- Sensitive Information Accessed: The compromised data included medical records, personal details, and potentially police reports related to the attack's victims. This sensitive information is protected under strict data protection laws and its unauthorized access represents a severe violation.
- Scale and Severity: The sheer number of individuals involved and the sensitive nature of the data accessed paint a picture of a major data security failure within the NHS. This incident highlights a systemic problem that requires immediate and decisive action. Keywords: "NHS data breach," "sensitive information," "patient data," "medical records," "personal data," "data protection."
How the Data Breach Occurred: Potential Causes and Failures in Security Protocols
The circumstances surrounding this NHS data breach are still under investigation, but several potential causes warrant consideration. Accidental access due to insufficient access controls remains a possibility. It is also crucial to examine whether deliberate breaches or system vulnerabilities played a role.
- Insufficient Access Controls: A lack of robust access control measures could have allowed unauthorized personnel to view sensitive files. This includes inadequate password protection, overly permissive access rights, and a lack of clear guidelines regarding data access.
- Human Error: Human error, such as clicking on malicious links or failing to adhere to security protocols, may have contributed to the breach.
- System Vulnerabilities: Existing vulnerabilities in the NHS IT systems could have been exploited to gain unauthorized access to patient data. Keywords: "data security," "access controls," "security protocols," "system vulnerabilities," "human error."
Consequences of the Data Breach: Impact on Victims and Public Trust
The impact of this NHS data breach extends far beyond the immediate violation of patient confidentiality. The victims of the Nottingham attack, already grappling with immense trauma, now face the added distress of knowing their highly sensitive information has been compromised.
- Impact on Victims: This breach can lead to emotional distress, identity theft, reputational damage, and a profound loss of trust in the healthcare system. The long-term psychological and emotional consequences for these individuals cannot be underestimated.
- Erosion of Public Trust: The incident further erodes public trust in the NHS's ability to safeguard sensitive patient data. This has broader implications for healthcare and public confidence in the overall security of personal information.
- Legal Ramifications: The NHS faces potential legal ramifications, including investigations and possible penalties for failing to uphold data protection regulations. Keywords: "patient confidentiality," "data protection," "public trust," "legal implications," "reputational damage."
The NHS Response: Investigation, Accountability, and Remedial Actions
The NHS has initiated an investigation into the data breach, promising to hold those responsible accountable. Disciplinary actions are expected, and remedial measures are underway to prevent future occurrences.
- Investigation and Accountability: A thorough investigation must uncover the full extent of the breach, identify the responsible parties, and determine the specific failures that led to this incident.
- Remedial Actions: The NHS needs to implement comprehensive improvements to its data security protocols, including stricter access controls, enhanced staff training, and regular security audits.
- Effectiveness of Response: The effectiveness of the NHS's response will be judged not only by its immediate actions but also by its long-term commitment to enhancing data security and regaining public trust. Keywords: "NHS response," "investigation," "accountability," "remedial actions," "data security improvements."
Lessons Learned and Future Prevention Strategies: Strengthening NHS Data Security
This NHS data breach serves as a stark reminder of the critical need for robust data security measures within the healthcare system.
- Strengthening Data Security: Implementing multi-factor authentication, enhancing encryption protocols, and regularly updating software are crucial steps.
- Staff Training: Comprehensive cybersecurity awareness training for all NHS staff is essential. This training should cover best practices for password management, phishing awareness, and safe data handling.
- Technological Advancements: Investing in advanced cybersecurity technologies, including intrusion detection systems and threat intelligence platforms, can significantly improve the NHS's ability to prevent and detect data breaches. Keywords: "data protection," "cybersecurity," "data security best practices," "staff training," "cybersecurity awareness."
Conclusion: Preventing Future NHS Data Breaches: A Call to Action
The NHS data breach involving the Nottingham attack victim files highlights the serious consequences of inadequate data security within the healthcare system. The scale of the breach, the sensitivity of the compromised information, and the potential impact on victims underscore the urgent need for decisive action. The NHS must demonstrate a clear commitment to strengthening its data security protocols, holding those responsible accountable, and implementing robust preventative measures. Protecting patient data is paramount. Demand stronger data security measures from the NHS to prevent future NHS data breaches. The future of patient confidentiality depends on it.
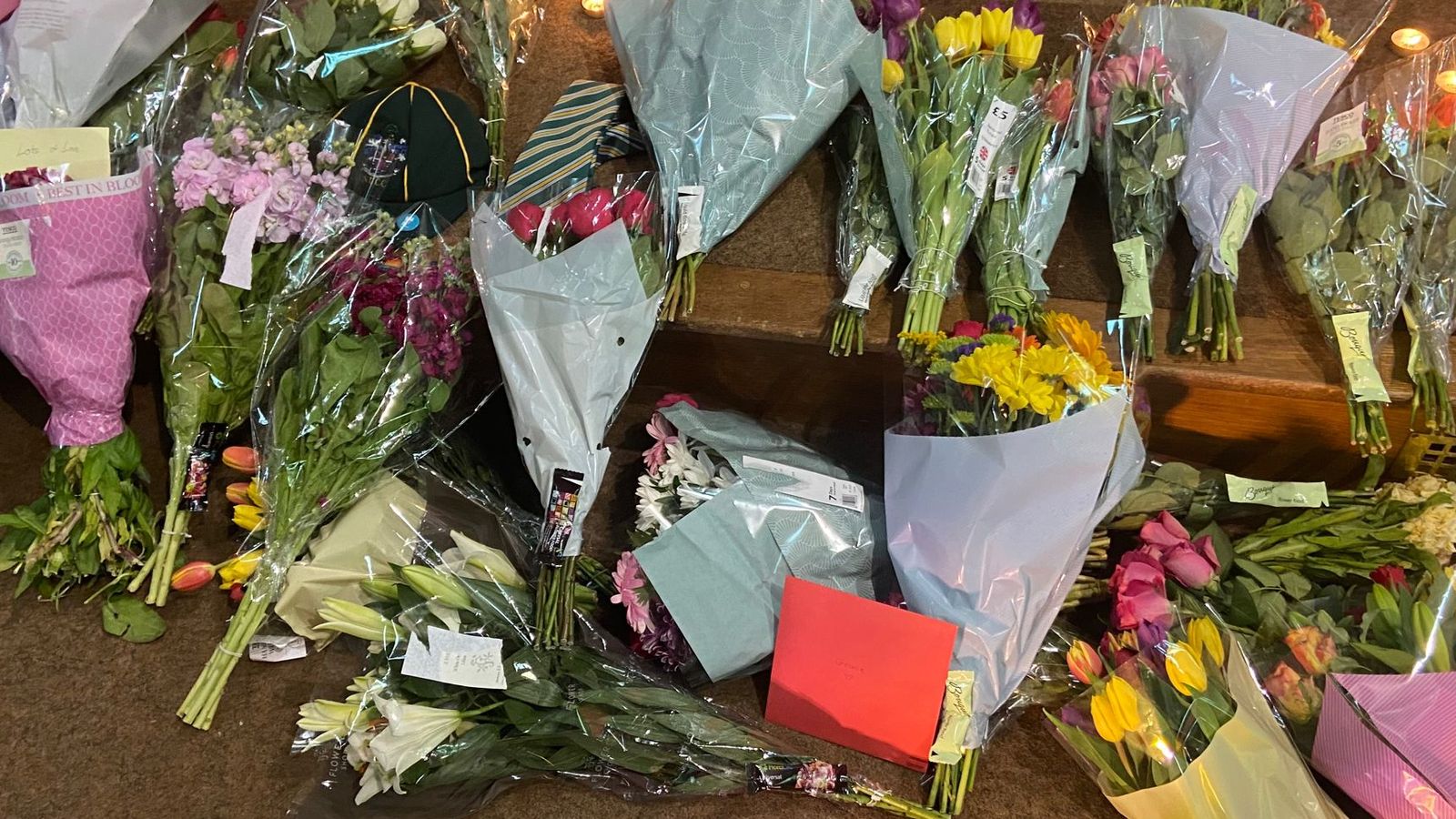
Featured Posts
-
 Nigerias Petrol Market Dangote Refinery And Nnpc Price Dynamics
May 10, 2025
Nigerias Petrol Market Dangote Refinery And Nnpc Price Dynamics
May 10, 2025 -
 Report Uk Plans To Restrict Visas From Pakistan Nigeria And Sri Lanka
May 10, 2025
Report Uk Plans To Restrict Visas From Pakistan Nigeria And Sri Lanka
May 10, 2025 -
 Elizabeth Hurleys Bikini Filled Maldives Trip
May 10, 2025
Elizabeth Hurleys Bikini Filled Maldives Trip
May 10, 2025 -
 Have Trumps Executive Orders Impacted Your Life As A Transgender Person We Want To Hear From You
May 10, 2025
Have Trumps Executive Orders Impacted Your Life As A Transgender Person We Want To Hear From You
May 10, 2025 -
 The Whats App Spyware Case Metas 168 Million Loss And What It Means
May 10, 2025
The Whats App Spyware Case Metas 168 Million Loss And What It Means
May 10, 2025
