Exec Office365 Breach: Crook Makes Millions, Feds Say

Table of Contents
The Mechanics of the Office365 Breach
The perpetrator in this high-profile Office365 breach employed a multi-pronged attack leveraging several common, yet highly effective, techniques. Understanding these methods is crucial for preventing similar incidents.
-
Detailed explanation of phishing techniques employed: The attacker likely utilized highly targeted phishing emails designed to mimic legitimate communications from trusted sources. These emails contained malicious links or attachments, leading victims to unknowingly compromise their Office365 credentials. Sophisticated phishing campaigns often employ social engineering tactics, leveraging current events or creating a sense of urgency to trick users into clicking. Keywords like "phishing email examples" and "advanced phishing techniques" can help understand the complexities involved.
-
Discussion of any exploited zero-day vulnerabilities: While specifics about exploited zero-day vulnerabilities (software flaws unknown to the vendor) are often kept confidential during active investigations, it's plausible that previously unknown weaknesses in Office365 or related applications were used to gain unauthorized access. This highlights the importance of staying updated on security patches and relying on a vendor's security updates.
-
Analysis of credential stuffing methods and their effectiveness: Credential stuffing involves using stolen username and password combinations from other data breaches to try to gain access to Office365 accounts. The sheer volume of attempted logins makes this a potent method, especially against accounts using weak or reused passwords. Addressing this threat requires strong password policies and multi-factor authentication.
-
Mention of any social engineering tactics used: Beyond phishing emails, social engineering tactics might have been employed. This could include pretexting (posing as someone else to gain information), baiting (offering something appealing to trick users), or quid pro quo (offering a service in exchange for sensitive information). These tactics often exploit human psychology to circumvent technical security measures. The keywords "social engineering attacks" and "human-factor vulnerabilities" are essential when considering this type of attack. Understanding how these techniques work is crucial for developing effective employee training programs.
The Financial Impact and Victim Count
The sheer scale of the financial impact of this Office365 breach is staggering. Federal authorities reported the perpetrator made millions of dollars, highlighting the lucrative nature of cybercrime. While the exact number of victims remains under investigation, reports suggest a significant number of individuals and organizations were affected.
-
Specific examples of financial losses incurred by victims (if available): The financial losses suffered by victims vary depending on the nature of the stolen data and the extent of the breach's impact. This can include direct financial losses from theft, costs associated with data recovery and remediation, legal fees, and reputational damage leading to loss of business.
-
Mention of any reputational damage suffered by victims: Beyond the financial losses, the reputational damage sustained by victims is substantial. A data breach can erode trust with customers and partners, leading to long-term financial consequences.
-
Discuss the legal ramifications for both the victims and the perpetrator: The victims might face legal action from customers and regulatory bodies for failing to adequately protect data. The perpetrator faces severe penalties, including hefty fines and imprisonment, under various federal cybercrime statutes. Keywords like "GDPR fines" and "data breach penalties" are relevant here.
Federal Investigation and Prosecution
The federal investigation into this Office365 breach is ongoing, but early reports suggest a concerted effort from multiple agencies, likely including the FBI and other relevant departments.
-
Details about the agencies involved in the investigation (FBI, etc.): Federal agencies specializing in cybercrime investigations collaborate to track down perpetrators, gather evidence, and build a case for prosecution.
-
Mention of any arrests or indictments: As the investigation progresses, arrests and indictments are expected. Publicly available information on this will be key.
-
Discussion of the potential penalties the perpetrator faces: The perpetrator faces severe penalties, including substantial fines, lengthy prison sentences, and restitution to victims. The severity of the penalties reflects the seriousness of the crime and acts as a deterrent to others.
Protecting Your Business from Office365 Breaches
Protecting your business from Office365 breaches requires a multi-layered approach combining technical safeguards and robust security awareness training.
-
Implement multi-factor authentication (MFA): MFA adds an extra layer of security, requiring more than just a password to access accounts. This significantly reduces the risk of unauthorized access, even if credentials are compromised.
-
Regularly update software and patches: Promptly applying software updates and security patches is vital to address known vulnerabilities.
-
Conduct employee security awareness training: Educate employees about phishing scams, social engineering tactics, and safe password practices. Regular training is crucial.
-
Use strong passwords and password management tools: Encourage the use of strong, unique passwords for all accounts and utilize password management tools to simplify this process.
-
Utilize advanced threat protection features within Office365: Office365 offers various advanced security features, including anti-phishing protection, malware detection, and data loss prevention (DLP) tools. Leverage these tools to their full extent.
-
Regular security audits and penetration testing: Regularly assess your security posture through audits and penetration testing to identify and address potential weaknesses.
Conclusion
The massive Office365 breach detailed above serves as a stark warning. The financial and reputational consequences of a successful cyberattack can be devastating. To prevent an Office365 breach and secure your Office365 environment, proactive security measures are paramount. Implement multi-factor authentication, enforce strong password policies, conduct regular security awareness training, and utilize the advanced threat protection features within Office365. Regularly assess your vulnerabilities through audits and penetration testing. Don't wait for an Office365 data breach to happen—take action now to protect your business.

Featured Posts
-
 Trump Demands Powells Removal From Federal Reserve
Apr 23, 2025
Trump Demands Powells Removal From Federal Reserve
Apr 23, 2025 -
 Record Breaking Power Yankees Hit 9 Home Runs Judge Leads The Charge
Apr 23, 2025
Record Breaking Power Yankees Hit 9 Home Runs Judge Leads The Charge
Apr 23, 2025 -
 Record Setting 9 Home Runs Yankees Dominate In 2025 Season Opener
Apr 23, 2025
Record Setting 9 Home Runs Yankees Dominate In 2025 Season Opener
Apr 23, 2025 -
 Yankees Opening Day Win A Winning Formula Revealed
Apr 23, 2025
Yankees Opening Day Win A Winning Formula Revealed
Apr 23, 2025 -
 Analyzing The Economics Top 5 Takeaways From The English Leaders Debate
Apr 23, 2025
Analyzing The Economics Top 5 Takeaways From The English Leaders Debate
Apr 23, 2025
Latest Posts
-
 The Lingering Threat Toxic Chemicals In Buildings Months After The Ohio Train Derailment
May 10, 2025
The Lingering Threat Toxic Chemicals In Buildings Months After The Ohio Train Derailment
May 10, 2025 -
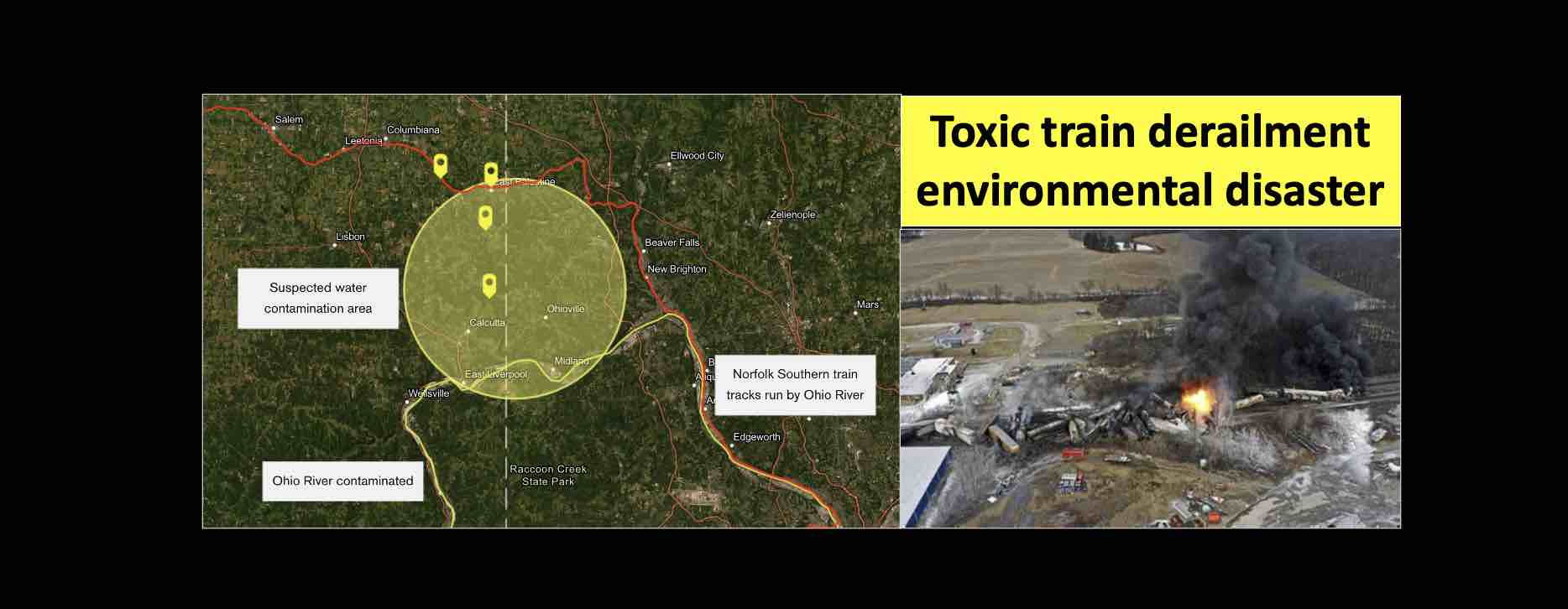 Toxic Chemical Residue From Ohio Train Disaster A Building By Building Assessment
May 10, 2025
Toxic Chemical Residue From Ohio Train Disaster A Building By Building Assessment
May 10, 2025 -
 Ohio Derailment Investigation Into Lingering Toxic Chemicals In Buildings
May 10, 2025
Ohio Derailment Investigation Into Lingering Toxic Chemicals In Buildings
May 10, 2025 -
 Analyzing Androids New Look Will It Win Over Gen Z
May 10, 2025
Analyzing Androids New Look Will It Win Over Gen Z
May 10, 2025 -
 The New Android Design A Gen Z Perspective
May 10, 2025
The New Android Design A Gen Z Perspective
May 10, 2025
