Federal Investigation: Millions Lost Due To Office365 Account Compromises
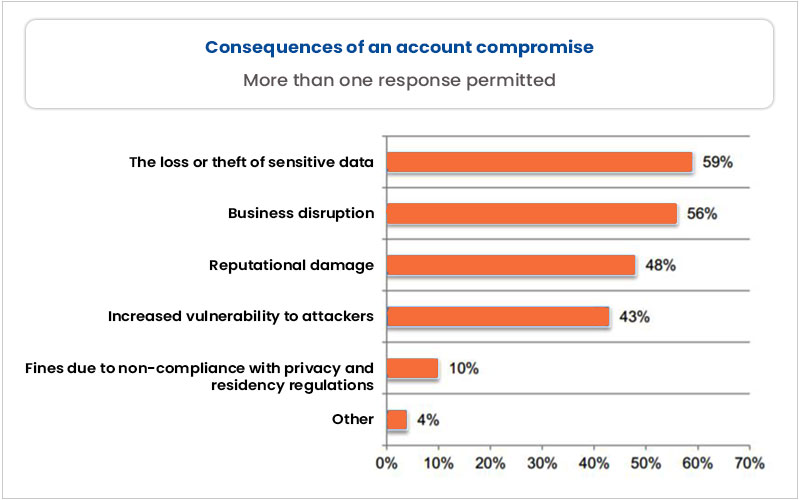
Table of Contents
The Scale of the Office365 Data Breach and Financial Losses
The financial fallout from these Office365 data breaches is staggering. While precise figures are still emerging from the ongoing federal investigation, early estimates suggest losses exceeding tens of millions of dollars across multiple agencies. The number of affected accounts remains under investigation, but initial reports indicate thousands of compromised accounts within various federal departments and agencies. This breach exposed highly sensitive data, including Personally Identifiable Information (PII), financial records, and intellectual property.
- Total monetary loss reported: Estimates currently exceed $XX million (exact figures pending investigation conclusion).
- Number of government agencies/departments affected: At least X agencies, with the potential for more as investigations continue.
- Types of data compromised: PII (names, addresses, social security numbers), financial data (bank account details, transaction records), intellectual property (research data, strategic plans), and confidential government communications.
- Geographic impact of the breach: The impact spans multiple states and potentially affects citizens nationwide.
Causes of Office365 Account Compromises: Phishing, Weak Passwords, and More
The Office365 account compromises were facilitated by a combination of factors, many of which are unfortunately common vulnerabilities. Cybercriminals exploited several attack vectors, primarily focusing on:
-
Phishing Scams: Sophisticated phishing emails, often mimicking legitimate communications from trusted sources, tricked employees into revealing their credentials. These emails often contained malicious links or attachments designed to install malware.
-
Weak or Reused Passwords: Many users employed weak, easily guessable passwords or reused the same password across multiple accounts. This made it relatively easy for attackers to gain access once they obtained credentials from one source.
-
Social Engineering: Attackers used social engineering tactics to manipulate employees into divulging sensitive information or granting access to their accounts.
-
Vulnerabilities in Third-Party Applications: Exploiting vulnerabilities in applications integrated with Office365 provided an entry point for attackers. This highlights the importance of regularly updating and securing all connected apps.
-
Malware and Ransomware Attacks: In some cases, malware was used to gain access to accounts and systems, enabling attackers to steal data or encrypt files for ransom.
-
Detailed explanation of phishing techniques: Attackers employed spear-phishing, targeting specific individuals with highly personalized emails.
-
Statistics on password weakness and reuse: Studies show a significant percentage of users use weak, easily guessable passwords, increasing vulnerability to brute-force attacks.
-
Examples of exploited vulnerabilities in third-party apps: Specific examples of vulnerable apps might not be publicly available due to ongoing investigations.
-
Discussion of malware and ransomware attacks: Malware such as keyloggers recorded user inputs, while ransomware encrypted data, demanding payment for decryption.
The Impact of Office365 Account Compromises on Federal Agencies and the Public
The impact of these Office365 account compromises extends far beyond financial losses. The breaches caused significant disruption to government operations, impacting essential services and potentially jeopardizing national security.
- Examples of disrupted government services: Delays in processing applications, disruptions to communication systems, and potential compromise of sensitive government projects.
- Risks of identity theft and financial fraud for citizens: Compromised PII poses a significant risk of identity theft, financial fraud, and other serious consequences for affected individuals.
- Long-term implications for public confidence in government: Breaches erode public trust and raise concerns about the government's ability to protect sensitive information.
- Potential legal repercussions for affected agencies: Agencies face potential legal action and regulatory penalties for failing to adequately protect sensitive data.
Strengthening Office365 Security: Best Practices and Preventative Measures
Preventing future Office365 account compromises requires a multi-faceted approach involving both technological and human factors. Organizations and individuals must prioritize the following:
-
Multi-Factor Authentication (MFA): Implement MFA to add an extra layer of security, requiring more than just a password to access accounts.
-
Strong Password Policies: Enforce strong, unique passwords and regularly change them. Password managers can help with this.
-
Security Awareness Training: Educate employees about phishing scams, social engineering techniques, and best practices for online security.
-
Regular Software Updates: Keep all software and applications, including Office365 and third-party integrations, updated with the latest security patches.
-
Robust Cybersecurity Protocols: Implement comprehensive cybersecurity protocols, including regular security audits and penetration testing.
-
Incident Response Planning: Develop and regularly test incident response plans to effectively manage and mitigate security incidents.
-
Secure Third-Party App Selection: Carefully vet and select secure third-party applications, ensuring they adhere to high security standards.
-
Step-by-step guide to enabling MFA: Detailed instructions are available on Microsoft's Office365 support website.
-
Best practices for creating strong, unique passwords: Use a combination of uppercase and lowercase letters, numbers, and symbols.
-
Tips for identifying and avoiding phishing scams: Look for suspicious email addresses, links, and attachments.
-
Importance of regular security audits and penetration testing: Regular assessments identify vulnerabilities before they can be exploited.
-
Recommendations for choosing secure third-party apps: Look for apps with strong security features and positive user reviews.
Conclusion: Protecting Against Future Office365 Account Compromises
The devastating impact of the recent Office365 account compromises underscores the critical need for proactive cybersecurity measures. The financial losses and reputational damage suffered by federal agencies highlight the severe consequences of inadequate security. By implementing the security best practices outlined above, organizations and individuals can significantly reduce their risk of falling victim to similar attacks. Don't become another statistic in the next Office365 breach. Implement strong security measures today to protect your data. Consider investing in professional cybersecurity services to ensure your Office365 environment is adequately protected. The cost of prevention is far less than the cost of a data breach.

Featured Posts
-
 Lindsey Graham On Russia Ceasefire Rejection Means Devastating Sanctions
May 22, 2025
Lindsey Graham On Russia Ceasefire Rejection Means Devastating Sanctions
May 22, 2025 -
 Remembering Adam Ramey A Tribute To The Dropout Kings Singer
May 22, 2025
Remembering Adam Ramey A Tribute To The Dropout Kings Singer
May 22, 2025 -
 Steelers Trade Proposal A Shocking Nfc Quarterback Acquisition
May 22, 2025
Steelers Trade Proposal A Shocking Nfc Quarterback Acquisition
May 22, 2025 -
 Thursdays Core Weave Crwv Stock Dip Factors Contributing To The Decrease
May 22, 2025
Thursdays Core Weave Crwv Stock Dip Factors Contributing To The Decrease
May 22, 2025 -
 7 Diem Nong Ket Noi Giao Thong Tp Hcm Long An
May 22, 2025
7 Diem Nong Ket Noi Giao Thong Tp Hcm Long An
May 22, 2025
