Federal Investigation: Millions Stolen Through Office365 Executive Email Compromise
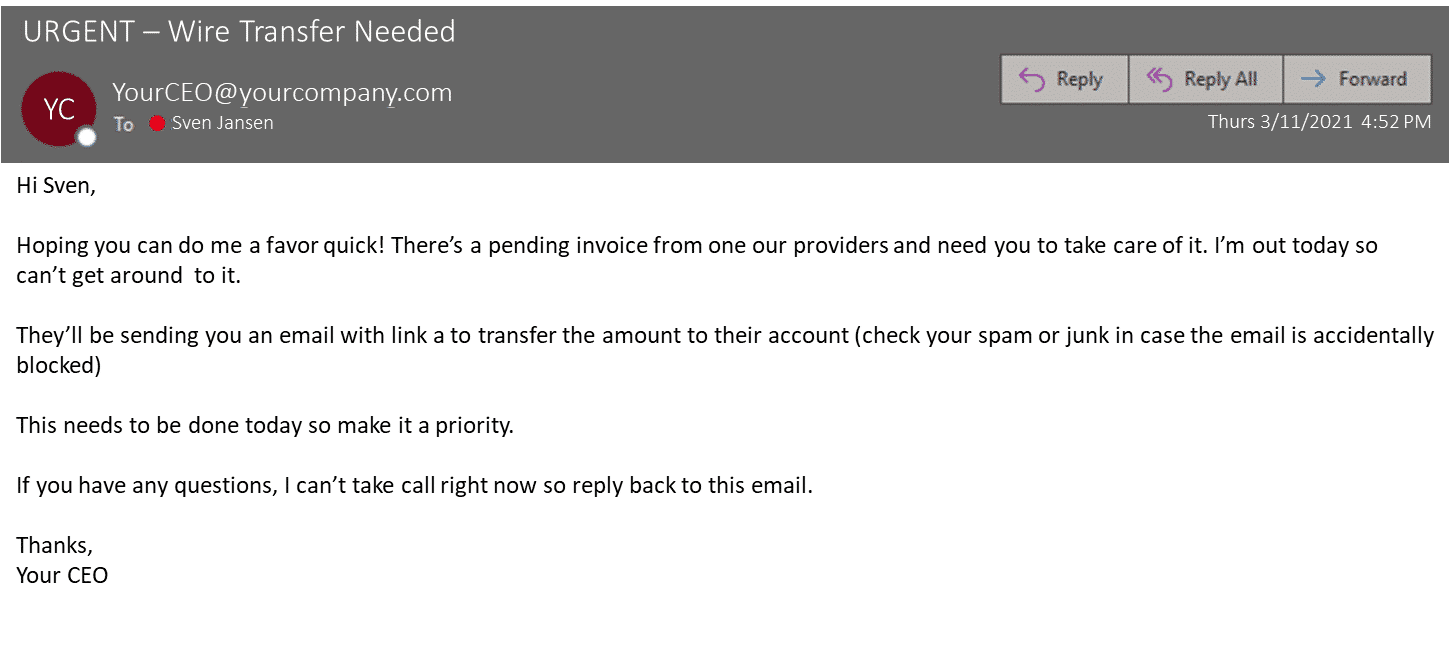
Table of Contents
The Modus Operandi of the Office365 Executive Email Compromise Scheme
The attackers behind this scheme employed a multi-pronged approach, combining sophisticated phishing and social engineering tactics with the exploitation of Office 365 vulnerabilities.
Phishing and Social Engineering Tactics
The attackers primarily relied on spear phishing, a highly targeted form of phishing where emails are crafted to appear as if they are from a trusted source, such as a CEO, CFO, or other high-ranking executive.
- Deceptive Emails: Emails often mimicked legitimate communication, including urgent requests for wire transfers, invoices, or sensitive financial information.
- Impersonation Tactics: Attackers skillfully impersonated executives, using their names and email addresses to create a sense of urgency and legitimacy.
- Urgency-Creating Language: Emails often contained phrases like "urgent," "immediate action required," or "confidential," designed to pressure recipients into acting quickly without verification.
- Attachment Types: Malicious attachments, disguised as invoices or other documents, were often used to deliver malware or gain access to systems.
Attackers gained access to legitimate email accounts by exploiting compromised credentials obtained through previous phishing attacks or password breaches, or by exploiting vulnerabilities within Office 365 itself.
Exploitation of Office365 Vulnerabilities
While specific vulnerabilities exploited in this particular federal investigation remain undisclosed for security reasons, several common Office 365 weaknesses are frequently targeted by attackers:
- Weak Passwords: Employees using easily guessable passwords or reusing passwords across multiple platforms are prime targets.
- Lack of Multi-Factor Authentication (MFA): MFA provides an extra layer of security, making it significantly harder for attackers to gain unauthorized access. Its absence is a major vulnerability.
- Unpatched Software: Outdated software contains known vulnerabilities that attackers can exploit. Regular updates are crucial for security.
- Insufficient User Training: A lack of employee awareness about phishing techniques makes them more susceptible to attacks.
Financial Transfers and Money Laundering
Once access was gained, attackers quickly initiated financial transfers.
- Wire Transfers: The preferred method, often targeting accounts with large sums of money.
- Cryptocurrency Transactions: Used to obscure the trail of stolen funds.
- Complex Money Laundering Schemes: Funds were often moved through multiple accounts and jurisdictions to make tracing difficult.
The complexity of tracing these funds and the international nature of the money laundering operations posed significant challenges for law enforcement.
Impact and Consequences of the Office365 Executive Email Compromise
The consequences of this Office 365 executive email compromise scheme were severe.
Financial Losses
The financial losses suffered by victims ranged significantly, but the overall impact was substantial, amounting to millions of dollars in total losses.
- Ranges of Money Lost: Losses varied from tens of thousands to hundreds of thousands of dollars per victim.
- Industry Sectors Most Affected: Businesses in finance, real estate, and technology were particularly vulnerable.
- Average Loss Per Victim: While the exact average is difficult to determine, the significant losses per victim highlight the severity of the problem.
Beyond direct financial loss, businesses faced long-term damage.
Reputational Damage and Legal Ramifications
The reputational damage from such breaches can be devastating.
- Negative Press: Public exposure of a security breach can severely damage a company's reputation and lead to loss of customer trust.
- Loss of Customer Trust: Clients may be hesitant to work with a company that has experienced a data breach.
- Potential Fines and Penalties: Organizations may face fines and penalties for failing to comply with data protection regulations.
Legal repercussions, including potential lawsuits from affected customers and regulatory investigations, can be costly and time-consuming.
Preventing Office365 Executive Email Compromise
Proactive security measures are crucial in preventing Office 365 executive email compromise.
Implementing Robust Security Measures
Businesses must implement robust security protocols to protect themselves:
- Multi-Factor Authentication (MFA): MFA is essential for securing accounts and preventing unauthorized access.
- Employee Training on Phishing Awareness: Regular training is vital to educate employees about phishing tactics and how to identify suspicious emails.
- Regular Software Updates: Keeping software up-to-date is crucial for patching vulnerabilities.
- Strong Password Policies: Enforce the use of strong, unique passwords and encourage password managers.
- Email Security Solutions: Advanced threat protection solutions can help identify and block malicious emails.
The Role of Email Security Solutions
Advanced email security solutions play a vital role:
- Anti-Phishing: These solutions use advanced techniques to detect and block phishing emails.
- Anti-Malware: They prevent malware from being delivered through malicious attachments.
- Anomaly Detection: They identify unusual email patterns that may indicate malicious activity.
Investing in a comprehensive email security solution is an investment in protecting your business.
Incident Response Planning
A well-defined incident response plan is crucial for minimizing losses if a compromise occurs:
- Steps to Take if a Compromise is Suspected: Establish clear procedures for identifying, containing, and remediating a security breach.
- Communication Protocols: Define how to communicate internally and externally in the event of a breach.
- Recovery Strategies: Develop plans for restoring systems and data after a security incident.
Having a robust incident response plan in place can significantly reduce the impact of a successful attack.
Conclusion
The federal investigation into the Office365 executive email compromise scheme highlights the critical need for robust cybersecurity measures. The scale of financial losses and the far-reaching consequences underscore the importance of proactive security practices. Key takeaways include the necessity of implementing multi-factor authentication, providing comprehensive employee training on phishing awareness, investing in advanced email security solutions like advanced threat protection, and establishing a well-defined incident response plan. Don't become another victim of Office365 executive email compromise. Implement robust security measures today to safeguard your business from this growing threat. For more information on securing your Office 365 environment and best practices, consult resources from reputable cybersecurity organizations and vendors.

Featured Posts
-
 Fox News Faces Defamation Lawsuit From Ray Epps Regarding Jan 6 Allegations
Apr 24, 2025
Fox News Faces Defamation Lawsuit From Ray Epps Regarding Jan 6 Allegations
Apr 24, 2025 -
 Millions Made From Office365 Hacks Federal Investigation Into Executive Email Breaches
Apr 24, 2025
Millions Made From Office365 Hacks Federal Investigation Into Executive Email Breaches
Apr 24, 2025 -
 The Bold And The Beautiful February 20th Spoilers Steffy Comforts Liam Poppy Warns Finn
Apr 24, 2025
The Bold And The Beautiful February 20th Spoilers Steffy Comforts Liam Poppy Warns Finn
Apr 24, 2025 -
 Finns Promise To Liam The Bold And The Beautiful Spoilers For Wednesday April 23
Apr 24, 2025
Finns Promise To Liam The Bold And The Beautiful Spoilers For Wednesday April 23
Apr 24, 2025 -
 Are High Stock Valuations A Concern Bof As Take
Apr 24, 2025
Are High Stock Valuations A Concern Bof As Take
Apr 24, 2025
