Millions Lost: Inside Job Or Sophisticated Office365 Hack?
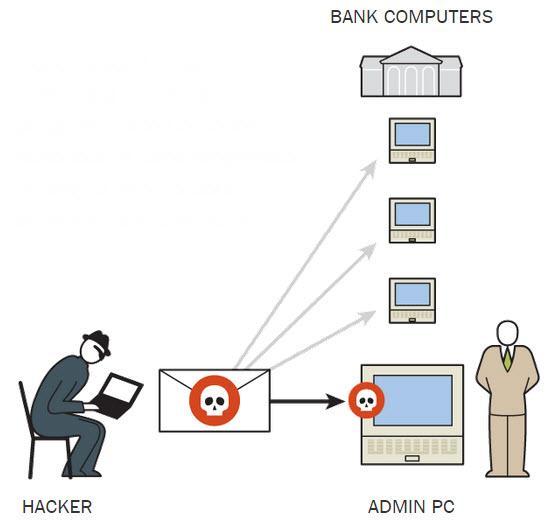
Table of Contents
The staggering reality is that millions of dollars are lost annually due to data breaches and financial losses stemming from Office365 hacks. Cybercriminals are constantly developing increasingly sophisticated methods to target Microsoft Office 365 environments, making robust security measures more critical than ever. This article delves into the complex question of whether such massive financial losses are the result of an inside job or a highly sophisticated external Office365 hack, examining the evidence and common attack vectors to help you understand and protect your organization. We'll explore the vulnerabilities, attack methods, and preventative measures to safeguard against both internal and external threats to your Office 365 environment.
H2: The Growing Threat of Office365 Hacks
The cloud, while offering many advantages, also introduces new challenges to security. Office365, a widely used platform, is unfortunately a prime target for cyberattacks. The increasing reliance on cloud-based services makes understanding these threats crucial for organizations of all sizes.
H3: Vulnerabilities in Office365:
Office365, like any system, has vulnerabilities that can be exploited. These include:
- Phishing Attacks: These remain a prevalent threat. Attackers craft convincing emails mimicking legitimate sources, tricking users into revealing credentials or downloading malware. Sophisticated phishing techniques include using cloned websites and exploiting brand trust. Statistics show a significant increase in successful phishing campaigns against Office365 users.
- Weak Passwords: Simple, easily guessable passwords are a major security weakness. Password reuse across multiple accounts amplifies the risk if one account is compromised. Implementing strong password policies and multi-factor authentication (MFA) is crucial.
- Unpatched Software: Outdated software often contains known vulnerabilities that hackers can exploit. Regular software updates and patching are essential for mitigating these risks. Delayed patching significantly increases the risk of an Office 365 security breach.
- Compromised Third-Party Apps: Many users integrate third-party apps with Office365. If these apps have security flaws, they can provide attackers with an entry point into your system. Carefully vetting and monitoring third-party app permissions is vital.
H3: The Rise of Advanced Persistent Threats (APTs):
Advanced Persistent Threats (APTs) are highly sophisticated, well-funded groups that often operate for extended periods, unnoticed. They target Office365 environments for long-term data exfiltration, often aiming for valuable intellectual property or sensitive customer information.
- Spear Phishing: APT groups often use highly targeted spear phishing campaigns, tailoring their attacks to specific individuals within an organization.
- Malware: They may deploy custom malware designed to evade detection, allowing them to maintain persistent access.
- Credential Stuffing: APT groups may attempt to use stolen credentials from other breaches to access Office365 accounts. Detecting and mitigating these attacks is challenging, requiring advanced security tools and expertise.
H2: The Inside Job Scenario: Signs and Indicators
While external threats are significant, internal threats pose a unique challenge. An insider with legitimate access can cause significant damage.
H3: Identifying Insider Threats:
Recognizing insider threats requires vigilance and monitoring. Warning signs include:
- Unusual Access Patterns: Accessing sensitive data outside of normal work hours or from unusual locations.
- Data Anomalies: Large or unusual data transfers, especially to external locations.
- Suspicious User Behavior: Employees exhibiting erratic behavior or changes in attitude. Implementing robust monitoring and logging systems is crucial for early detection.
H3: Motives and Prevention:
Motives for insider threats can vary:
- Financial Gain: Selling sensitive data to competitors.
- Revenge: Malicious intent due to workplace disputes.
- Espionage: Data theft for competitive advantage.
Preventing insider threats involves:
- Thorough Background Checks: Vetting potential employees carefully.
- Strict Access Control Policies: Implementing the principle of least privilege.
- Comprehensive Employee Security Awareness Training: Educating employees about security risks and best practices.
H2: Sophisticated External Office365 Hack Scenarios
External attackers employ increasingly sophisticated techniques to breach Office365.
H3: Advanced Phishing and Social Engineering:
Modern phishing attacks are highly sophisticated, often using techniques to bypass multi-factor authentication (MFA).
- Advanced Phishing Techniques: Mimicking legitimate login pages, using deceptive email subject lines, and exploiting social engineering principles.
- Bypassing MFA: Attackers may use techniques like SIM swapping or exploiting vulnerabilities in MFA implementations to gain access.
H3: Exploiting Zero-Day Vulnerabilities:
Zero-day exploits target newly discovered vulnerabilities before patches are released. This requires proactive measures:
- Proactive Patching: Regularly updating software to address known vulnerabilities.
- Vulnerability Management: Continuously monitoring for and addressing newly discovered vulnerabilities.
Conclusion:
The threat landscape surrounding Office365 is dynamic and evolving. Both internal and external threats pose significant risks, potentially leading to "millions lost" in financial and reputational damage. Understanding the key differences between a sophisticated Office365 hack and an inside job is crucial for developing a comprehensive security strategy. Robust security requires a multi-layered approach, including strong passwords, multi-factor authentication, regular software updates, proactive vulnerability management, employee security awareness training, and rigorous incident response planning. Don't wait until it's too late. Take proactive steps to enhance your Office365 security posture today. Learn more about Office365 security best practices or consult with cybersecurity experts to protect your organization from the devastating consequences of an Office365 compromise. Preventing an Office365 hack is an investment that can save your organization millions.

Featured Posts
-
 Dc Black Pride Celebrating Culture Embracing Protest
May 26, 2025
Dc Black Pride Celebrating Culture Embracing Protest
May 26, 2025 -
 Rtl Et Laurence Melys Une Voix Pour Le Cyclisme Feminin
May 26, 2025
Rtl Et Laurence Melys Une Voix Pour Le Cyclisme Feminin
May 26, 2025 -
 Analyzing The F1 Drivers Press Conference Insights And Predictions
May 26, 2025
Analyzing The F1 Drivers Press Conference Insights And Predictions
May 26, 2025 -
 Amazon Primes Etoile Gideon Glick Steals The Show
May 26, 2025
Amazon Primes Etoile Gideon Glick Steals The Show
May 26, 2025 -
 Mercedes Performance Boost George Russells Key Strategic Choice
May 26, 2025
Mercedes Performance Boost George Russells Key Strategic Choice
May 26, 2025
