Office365 Inbox Hacks Net Millions For Cybercriminal, Authorities Say
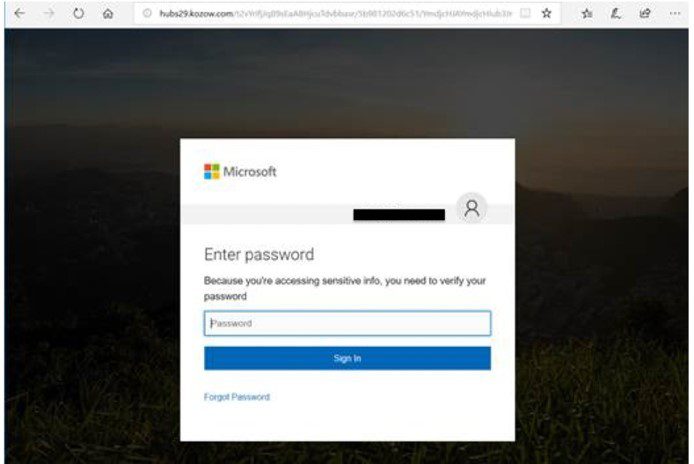
Table of Contents
The Methods Behind the Millions: How Cybercriminals Target Office365
Cybercriminals employ a range of sophisticated techniques to breach the security of Office365 accounts. Understanding these methods is the first step towards effective protection.
Phishing and Spear Phishing Attacks
Phishing attacks targeting Office365 users have evolved significantly. They're no longer simply generic emails promising large sums of money; instead, they utilize highly targeted and personalized approaches. Spear phishing, in particular, is a highly effective tactic. Attackers meticulously research their victims, impersonating known contacts, colleagues, or even legitimate organizations. These emails often contain seemingly innocuous attachments or links designed to deliver malware or steal credentials.
- Examples of subject lines used in phishing attacks: "Urgent Invoice," "Your Password has Expired," "Security Alert," "Meeting Minutes Attached."
- Examples of malicious attachments and links: Documents with embedded macros, shortened URLs leading to phishing websites, seemingly legitimate software updates.
- Statistics: Recent studies show that a significant percentage of Office365 users fall victim to phishing attacks each year, highlighting the effectiveness of these tactics and the need for robust security awareness training.
Exploiting Weak Passwords and Credentials
Stolen credentials are a major pathway for gaining access to Office365 accounts. Cybercriminals utilize various methods, including brute-force attacks, credential stuffing, and phishing to acquire login details. Password reuse, a common practice among users, significantly increases the risk of a successful breach. If a password is compromised on one platform, attackers can attempt to use it to access other accounts, including Office365.
- Tips for creating strong, unique passwords: Use a password manager, create passwords that are at least 12 characters long, include a mix of uppercase and lowercase letters, numbers, and symbols, and avoid using personal information.
- Statistics: The frequency of successful credential stuffing attacks underscores the importance of strong password hygiene and multi-factor authentication (MFA). Many attacks leverage stolen credentials from other data breaches.
Malware and Ransomware Infections
Malware plays a crucial role in many Office365 attacks. Trojans, keyloggers, and other malicious software can be used to steal credentials, monitor user activity, and exfiltrate sensitive data. Once access is gained, ransomware can be deployed, encrypting files and demanding a ransom for their release. This can have devastating consequences for businesses and individuals alike.
- Types of malware commonly used: Trojans disguised as legitimate attachments, keyloggers that record keystrokes, and remote access trojans (RATs) that give attackers complete control over the infected system.
- Steps businesses can take to prevent ransomware infections: Regularly back up data, implement robust endpoint protection software, and educate employees on safe email practices.
The Devastating Consequences: Financial and Reputational Damage
The impact of a successful Office365 inbox hack extends far beyond the initial compromise. The consequences can be financially crippling and severely damage a company's reputation.
Financial Losses
Data breaches and ransomware attacks can result in significant financial losses. These losses include direct costs such as ransom payments, recovery and remediation expenses, legal fees, and lost revenue due to downtime. The costs associated with restoring data, notifying affected individuals, and repairing damaged reputations can be substantial.
- Examples of financial losses: Millions of dollars in ransom payments, tens of thousands of dollars in legal fees, significant loss of revenue due to business disruption.
- Statistics: The average cost of a data breach continues to rise, highlighting the importance of proactive security measures.
Reputational Damage
A data breach severely impacts a company's reputation and brand image. Loss of customer trust, negative media coverage, and potential legal repercussions can lead to long-term damage. Customers may be hesitant to do business with a company that has suffered a security breach, leading to lost sales and revenue.
- Strategies for mitigating reputational damage: A swift and transparent response, proactive communication with customers and stakeholders, and a commitment to improving security measures.
- The importance of a proactive communication strategy: Openly communicating with affected parties and stakeholders demonstrates responsibility and builds trust.
Protecting Your Office365 Inbox: Essential Security Measures
Protecting your Office365 inbox requires a multi-layered approach that combines technical solutions and employee education.
Multi-Factor Authentication (MFA)
MFA is a critical security measure that adds an extra layer of protection beyond passwords. By requiring a second form of verification, MFA significantly reduces the risk of unauthorized access, even if passwords are compromised.
- Benefits of using MFA for Office365: Increased security, reduced risk of unauthorized access, compliance with industry regulations.
- Different MFA options: SMS codes, authenticator apps (like Google Authenticator or Microsoft Authenticator), security keys.
Security Awareness Training
Employee education is paramount in preventing phishing attacks. Regular security awareness training equips employees with the knowledge and skills to identify and avoid phishing attempts, malicious links, and unsafe attachments.
- Key topics to cover in security awareness training: Phishing recognition, password security, safe email practices, malware awareness.
- Methods for conducting effective training: Interactive simulations, phishing awareness campaigns, regular training sessions.
Advanced Threat Protection (ATP)
Office 365 Advanced Threat Protection (ATP) provides advanced protection against sophisticated threats, including phishing, malware, and ransomware. ATP uses machine learning and other advanced techniques to identify and block malicious emails and attachments before they reach users' inboxes.
- Key features of Office 365 ATP: Anti-phishing, anti-malware, anti-spam, safe links, and safe attachments.
- The cost and benefits of using ATP: While there's a cost associated with ATP, the benefits far outweigh the expense, given the potential financial and reputational damage from a successful breach.
Conclusion
Office365 inbox hacks are a significant and growing threat, costing businesses and individuals millions of dollars annually. By understanding the methods employed by cybercriminals, the devastating consequences of a successful attack, and the crucial security measures available, you can significantly reduce your risk. Implementing multi-factor authentication (MFA), conducting regular security awareness training, and utilizing advanced threat protection like Office 365 ATP are crucial steps in securing your Office365 environment. Don't wait until it's too late – take action today to secure your Office365 inbox and prevent becoming the next victim of these lucrative attacks. Learn more about bolstering your Office365 security and protecting against costly inbox hacks now.

Featured Posts
-
 Fate Of Abc News Show Uncertain Following Mass Layoffs
May 20, 2025
Fate Of Abc News Show Uncertain Following Mass Layoffs
May 20, 2025 -
 Suki Waterhouses Met Gala 2025 Dress A Bold Black Tuxedo With Sideboob Detail
May 20, 2025
Suki Waterhouses Met Gala 2025 Dress A Bold Black Tuxedo With Sideboob Detail
May 20, 2025 -
 Sxolikos Ekfovismos I Ypothesi Giakoymaki Kai Oi Synepeies Toy Bullying
May 20, 2025
Sxolikos Ekfovismos I Ypothesi Giakoymaki Kai Oi Synepeies Toy Bullying
May 20, 2025 -
 The Inside Story How Michael Strahan Secured A High Profile Interview During A Ratings War
May 20, 2025
The Inside Story How Michael Strahan Secured A High Profile Interview During A Ratings War
May 20, 2025 -
 Suki Waterhouse Calls Fans Twinks On Tik Tok The Video And The Reaction
May 20, 2025
Suki Waterhouse Calls Fans Twinks On Tik Tok The Video And The Reaction
May 20, 2025
