Office365 Security Breach: Millions Stolen In Executive Email Compromise
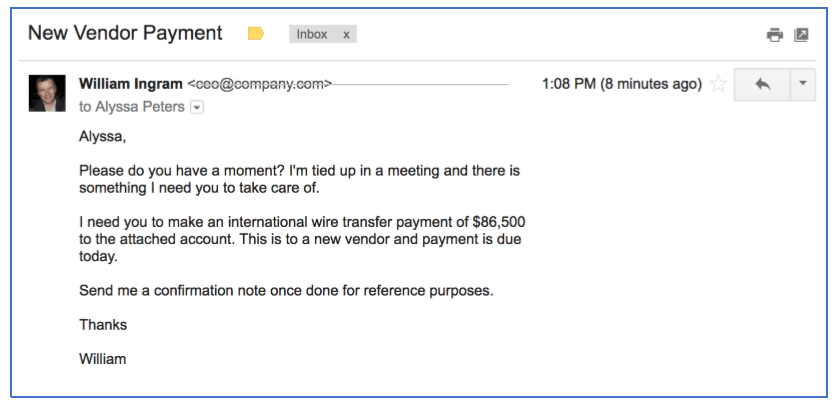
Table of Contents
Understanding Executive Email Compromise (EEC) in Office365
Executive email compromise, often referred to as CEO fraud or business email compromise (BEC), is a sophisticated form of phishing that specifically targets high-level executives within an organization. Attackers leverage the trust and authority associated with these individuals to manipulate them into performing actions that lead to financial loss or data theft. These aren't your typical spam emails; they are highly personalized and meticulously crafted to appear legitimate. The attackers often spend significant time researching their target, gathering information to make their phishing attempts even more convincing. This technique, sometimes called "whaling," focuses on "big fish" – the executives who have access to significant funds and sensitive information.
- EEC attacks often mimic legitimate communications from trusted sources, such as board members, clients, or even the CEO's own staff.
- Phishing emails are highly personalized and tailored to the target, referencing specific projects, transactions, or upcoming events.
- Attackers may gain access to financial systems, initiate fraudulent wire transfers, or steal sensitive client data, impacting not only the company but also its reputation with its clientele.
- The financial losses associated with EEC can be devastating, running into millions of dollars in some cases, crippling even large organizations.
Common Vulnerabilities Exploited in Office365 Breaches
While Office365 offers robust security features, several vulnerabilities are frequently exploited by attackers. Understanding these weaknesses is the first step towards effective mitigation. Many breaches stem from human error or neglecting basic security best practices.
- Weak or reused passwords: Many employees use weak, easily guessable passwords or reuse the same password across multiple accounts. This makes it simple for attackers to gain access.
- Lack of multi-factor authentication (MFA): MFA adds an extra layer of security, requiring users to provide multiple forms of authentication before accessing their accounts. The absence of MFA significantly increases vulnerability.
- Outdated software and operating systems: Failing to regularly update software and operating systems leaves systems open to known exploits and vulnerabilities that attackers can easily leverage.
- Insufficient security awareness training for employees: Many employees lack the awareness and training to recognize and respond to phishing emails, making them susceptible to attacks.
- Exploiting vulnerabilities in third-party applications integrated with Office365: Third-party applications often have their own security vulnerabilities that can be used as entry points for attackers.
Protecting Your Organization from Office365 Security Breaches
Protecting your organization from Office365 security breaches requires a multi-layered approach combining technology and employee education. Robust security practices are paramount.
- Enforce strong password policies and multi-factor authentication (MFA): Implement strong password policies requiring complex passwords and regularly changing them. Mandate MFA for all users, significantly reducing the risk of unauthorized access.
- Implement comprehensive security awareness training programs: Regularly train employees to identify and avoid phishing attempts, recognize malicious links and attachments, and report suspicious emails. Simulate phishing attacks to assess employee preparedness.
- Regularly update software and patches: Ensure all software and operating systems are up-to-date with the latest security patches to close known vulnerabilities.
- Utilize advanced threat protection features offered by Office365: Leverage Office365's advanced threat protection features, including anti-phishing, anti-malware, and anti-ransomware capabilities.
- Implement data loss prevention (DLP) measures: Implement DLP measures to prevent sensitive data from leaving the organization's network without authorization.
- Regularly back up your data: Regular and secure data backups are crucial for recovery in case of a successful attack or ransomware infection.
- Develop a robust incident response plan: Have a well-defined incident response plan in place to quickly and effectively address security breaches when they occur. This includes procedures for identifying, containing, and remediating the attack, as well as communicating with stakeholders.
The Cost of an Office365 Security Breach – More Than Just Money
The cost of an Office365 security breach extends far beyond the immediate financial losses. The reputational damage and legal ramifications can be equally, if not more, devastating.
- Loss of customer trust and brand reputation: A security breach can severely damage your brand reputation, leading to a loss of customer trust and potential business.
- Legal fees and potential fines for non-compliance (GDPR, CCPA, etc.): Failure to comply with data protection regulations like GDPR and CCPA can result in significant legal fees and substantial fines.
- Damage to stakeholder relationships: A breach can damage relationships with investors, partners, and other stakeholders, impacting future collaborations.
- Potential for further attacks and data breaches: A successful attack can leave your organization vulnerable to further attacks and data breaches, leading to a cycle of increasingly damaging incidents.
Conclusion
Office365 security breaches, particularly executive email compromise, pose a significant and escalating threat to businesses. The financial losses, reputational damage, and legal repercussions can be catastrophic. Proactively strengthening your Office365 security posture is not just advisable—it’s essential. Implement robust security measures, including multi-factor authentication, regular security updates, and comprehensive employee training to safeguard your organization from the devastating consequences of an Office365 security breach and executive email compromise. Don't become another statistic; prioritize your Office365 security today. Invest in robust email security solutions and advanced threat protection to mitigate the risk of an Office365 security breach.

Featured Posts
-
 Prince Andrews Temper Explosive Outbursts Detailed By Former Royal Staff
May 11, 2025
Prince Andrews Temper Explosive Outbursts Detailed By Former Royal Staff
May 11, 2025 -
 Atomnye Podlodki Putin Obratilsya K Dzhonsonu
May 11, 2025
Atomnye Podlodki Putin Obratilsya K Dzhonsonu
May 11, 2025 -
 The Conor Mc Gregor Fox News Saga Key Moments And Public Reactions
May 11, 2025
The Conor Mc Gregor Fox News Saga Key Moments And Public Reactions
May 11, 2025 -
 Pentagons Greenland Proposal Concerns And Analysis Of Us Arctic Ambitions
May 11, 2025
Pentagons Greenland Proposal Concerns And Analysis Of Us Arctic Ambitions
May 11, 2025 -
 Sir Bradley Wiggins Opens Up His Post Cycling Addiction And Financial Difficulties
May 11, 2025
Sir Bradley Wiggins Opens Up His Post Cycling Addiction And Financial Difficulties
May 11, 2025
