Transferred Data: A Comprehensive Guide

Table of Contents
Understanding Different Types of Transferred Data
Transferred data encompasses a wide range of information exchanged across various platforms and systems. Let's explore some key categories:
File Transfers
File Transfer Protocol (FTP), Secure File Transfer Protocol (SFTP), and Secure Copy Protocol (SCP) are common methods for transferring files between computers. Each offers varying levels of security and speed.
- FTP: A simple protocol, but lacks inherent security, making it vulnerable to interception. Suitable only for transferring non-sensitive data over trusted networks.
- SFTP: A secure alternative to FTP, employing SSH encryption to protect transferred data during transit. Offers better security and is widely preferred for sensitive files.
- SCP: Another secure shell-based protocol offering similar security to SFTP but often simpler to implement.
Choosing the right method depends on the sensitivity of your data and network infrastructure. Consider factors such as speed, security protocols, file size limitations, and compatibility when selecting a file transfer method.
Database Migrations
Database migration involves transferring data from one database system to another. This process often includes schema changes (altering the database structure), data cleansing (removing inconsistencies and errors), and data transformation (converting data formats).
- Data Integrity: Maintaining data accuracy and consistency throughout the migration is paramount. Thorough testing is essential.
- Downtime Minimization: Strategies like phased migration or using replication techniques can minimize service disruptions.
- Data Transformation Tools: Specialized tools automate and streamline the complex process of transforming data between different database systems.
- Backup and Recovery Strategies: Implementing robust backup and recovery plans is crucial to mitigate potential data loss during migration.
Cloud Data Transfers
Transferring data to and from cloud storage services like AWS S3, Azure Blob Storage, and Google Cloud Storage requires careful consideration of several factors.
- Cloud Storage Providers: Each provider offers varying features, pricing, and performance characteristics. Selecting the right provider depends on your specific needs.
- Transfer Speeds: Bandwidth availability significantly impacts transfer speed. Consider using direct connect options for faster transfers of large datasets.
- Data Encryption: Employing encryption both in transit and at rest is crucial to protect your data in the cloud.
- Cost Optimization Strategies: Understanding pricing models and leveraging features like data lifecycle management can help optimize cloud storage costs.
Network Data Transfers
Data transfer within a network relies on protocols like TCP/IP to ensure reliable and ordered delivery of data packets. Managing bandwidth and ensuring network security are crucial aspects.
- Network Topologies: The physical and logical layout of your network impacts transfer speeds and efficiency.
- Bandwidth Limitations: Understanding your network's bandwidth capacity helps prevent congestion and ensures optimal transfer speeds.
- Network Security Protocols: Implementing firewalls, intrusion detection systems, and other security measures protects your network from unauthorized access and data breaches.
- Data Loss Prevention (DLP): Implementing DLP measures, such as network segmentation and data encryption, is crucial to prevent data loss during network transfers.
Ensuring Secure Data Transfer
Protecting transferred data is crucial. Here’s how:
Encryption Methods
Encryption is a cornerstone of secure data transfer. Various encryption techniques exist:
- SSL/TLS: Widely used for secure communication over the internet, encrypting data in transit.
- AES: A strong symmetric encryption algorithm offering robust protection for sensitive data.
- PGP: Provides confidentiality and authentication for email and file transfers.
Choosing the appropriate encryption method depends on the sensitivity of the data and the security requirements of your application. Proper key management is essential.
Access Control and Authorization
Restricting access to transferred data is vital. Robust access control mechanisms are essential:
- Role-Based Access Control (RBAC): Grants access based on user roles and responsibilities.
- Authentication Protocols: Employing strong authentication methods like multi-factor authentication enhances security.
- Access Logs: Maintaining detailed logs of all access attempts allows for monitoring and auditing purposes.
Data Loss Prevention (DLP)
Preventing data loss during transfer requires a multi-faceted approach:
- Data Backup and Recovery: Regular backups and a robust recovery plan mitigate the impact of data loss.
- Data Redundancy Techniques: Implementing redundancy, such as RAID storage, protects against data loss due to hardware failure.
- Error Detection and Correction Codes: These codes help identify and correct errors during data transmission.
Optimizing Data Transfer Performance
Optimizing data transfer speeds is essential for efficiency.
Network Optimization
Several techniques improve network performance:
- Bandwidth Management Techniques: Prioritizing data traffic and optimizing network configurations can improve transfer speeds.
- Quality of Service (QoS): QoS allows you to prioritize specific types of data traffic, ensuring that critical data transfers are not delayed.
- Network Monitoring Tools: Tools monitor network performance, identify bottlenecks, and help optimize network configuration.
Compression Techniques
Data compression reduces file sizes, speeding up transfers and saving storage space:
- Lossless Compression: Algorithms like zip, gzip, and bzip2 allow for perfect data reconstruction after compression.
- Lossy Compression: Techniques like JPEG and MP3 reduce file size but result in some data loss. Appropriate for situations where some data loss is acceptable.
- Compression Ratios: Understanding compression ratios helps determine the effectiveness of different compression algorithms.
Transfer Protocols
The choice of protocol directly impacts speed and security:
- Protocol Comparison: FTP is faster but less secure than SFTP or SCP. HTTP is suitable for web-based transfers.
- Choosing the Right Protocol: The best protocol depends on the specific needs of the data transfer. Consider factors such as security requirements, speed, and compatibility.
Conclusion
Mastering transferred data is crucial for maintaining data integrity, ensuring business continuity, and complying with regulations. This guide has explored various aspects of transferred data, from understanding different types and implementing secure protocols to optimizing performance. By implementing the best practices discussed, you can significantly improve the security and efficiency of your data transfer operations. For further resources on data transfer optimization and security best practices, explore articles and tools from leading cybersecurity providers and cloud services. Efficiently managing data transfers is essential for staying competitive in today's data-driven world.

Featured Posts
-
 The China Factor Examining The Automotive Industrys Dependence And Risks
May 08, 2025
The China Factor Examining The Automotive Industrys Dependence And Risks
May 08, 2025 -
 How To Break Bread With Scholars Tips For Effective Academic Engagement
May 08, 2025
How To Break Bread With Scholars Tips For Effective Academic Engagement
May 08, 2025 -
 Bitcoin Madenciligi Eskisi Gibi Karli Degil Mi
May 08, 2025
Bitcoin Madenciligi Eskisi Gibi Karli Degil Mi
May 08, 2025 -
 Psl 10 Ticket Sales Begin Today
May 08, 2025
Psl 10 Ticket Sales Begin Today
May 08, 2025 -
 The Conclave Begins Electing The Next Pope
May 08, 2025
The Conclave Begins Electing The Next Pope
May 08, 2025
Latest Posts
-
 Bayern Munich Vs Eintracht Frankfurt Match Preview And Prediction
May 09, 2025
Bayern Munich Vs Eintracht Frankfurt Match Preview And Prediction
May 09, 2025 -
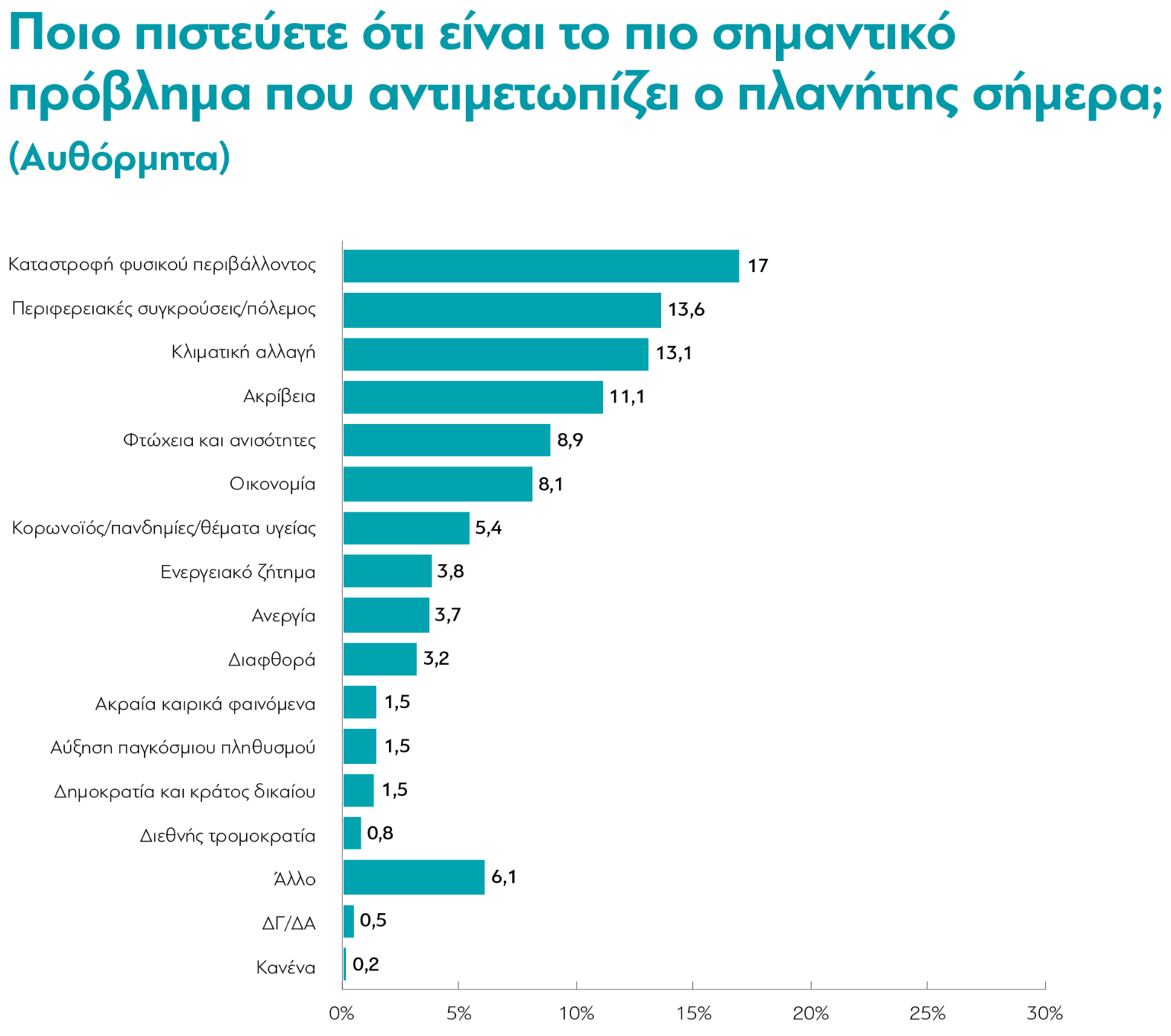 I Klimatiki Allagi Kai Ta Xamila Xionia Sta Imalaia
May 09, 2025
I Klimatiki Allagi Kai Ta Xamila Xionia Sta Imalaia
May 09, 2025 -
 Nepogoda V Yaroslavskoy Oblasti Gotovnost K Snegopadam
May 09, 2025
Nepogoda V Yaroslavskoy Oblasti Gotovnost K Snegopadam
May 09, 2025 -
 Imalaia Elaxista Xionia Se 23etia Anisyxia Gia To Mellon
May 09, 2025
Imalaia Elaxista Xionia Se 23etia Anisyxia Gia To Mellon
May 09, 2025 -
 Silniy Snegopad Ostavil 45 000 Chelovek V Sverdlovskoy Oblasti Bez Sveta
May 09, 2025
Silniy Snegopad Ostavil 45 000 Chelovek V Sverdlovskoy Oblasti Bez Sveta
May 09, 2025
