Cybercriminal Makes Millions Targeting Executive Office365 Accounts
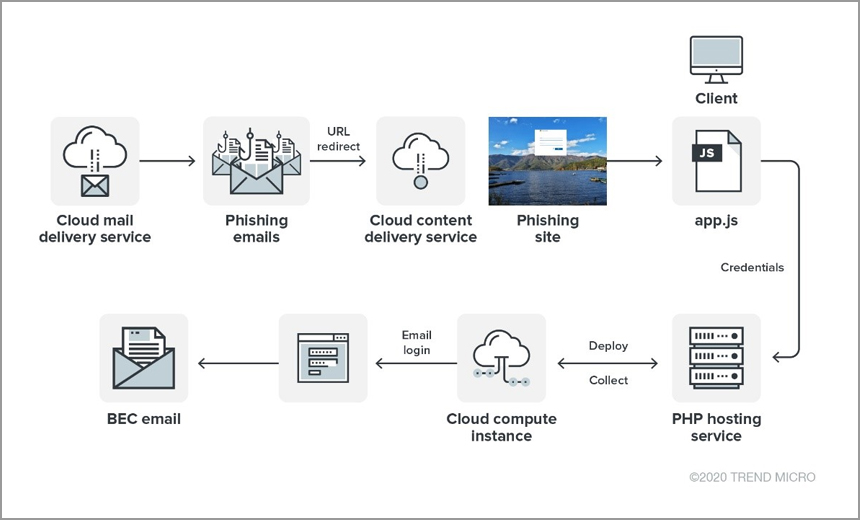
Table of Contents
The Sophistication of the Attacks
This wasn't your average phishing scam. The attacks showcased a level of sophistication far beyond simple email traps. The cybercriminal employed advanced techniques, including spear phishing, credential stuffing, and potentially exploiting zero-day vulnerabilities to gain unauthorized access. These attacks weren't random; they were highly targeted, focusing on executives due to their access to sensitive financial and strategic information.
- Highly Personalized Spear Phishing: Emails were crafted with meticulous detail, mimicking trusted sources like board members or known business partners. These emails contained convincing narratives and attachments designed to entice the recipient to click malicious links or download malware.
- Credential Stuffing and Weak Passwords: The criminal likely used lists of stolen credentials obtained from previous data breaches to attempt logins to executive accounts. Reused passwords and weak password choices made these accounts particularly vulnerable.
- Malware and Persistent Access: Once access was gained, malware was often deployed to maintain persistent access, allowing the criminal to monitor activity and exfiltrate data over time.
- Social Engineering: The attacker likely leveraged social engineering tactics, such as creating a sense of urgency or exploiting psychological vulnerabilities to manipulate victims into revealing sensitive information or performing actions they wouldn't normally do.
The Financial Impact of the Breaches
The financial consequences of these breaches are staggering. Targeted companies experienced millions of dollars in direct financial losses, often due to fraudulent wire transfers initiated from compromised accounts. However, the cost extends far beyond the immediate financial theft.
- Direct Financial Theft: Millions were directly stolen through unauthorized transactions, impacting company funds and potentially investor investments.
- Data Breach Response and Remediation: The costs associated with investigating the breach, notifying affected parties, and implementing remediation measures can reach hundreds of thousands, if not millions, of dollars.
- Reputational Damage: A data breach severely impacts a company's reputation, leading to a loss of customer trust and potential damage to brand image. This can result in lost business and decreased profitability.
- Legal Fees and Regulatory Fines: Companies face legal battles, potential lawsuits from affected individuals, and substantial fines from regulatory bodies for non-compliance with data protection regulations like GDPR or CCPA.
- Long-Term Impact on Valuation: The long-term impact on company valuation and investor confidence can be significant, leading to decreased stock prices and difficulty attracting future investment.
Methods Used to Secure Executive Office 365 Accounts
Preventing such attacks requires a multi-layered approach focusing on proactive security measures and employee training. Robust cybersecurity practices are paramount in protecting sensitive information and preventing financial losses. Here are some key strategies:
- Multi-Factor Authentication (MFA): Implementing MFA for all Office 365 accounts, especially those belonging to executives, is crucial. This adds an extra layer of security, making it significantly harder for attackers to gain access even if they have stolen passwords.
- Regular Security Awareness Training: Conduct regular training sessions for all employees, particularly executives, to educate them about phishing scams, social engineering tactics, and best practices for online security.
- Strong Password Policies: Enforce strong password policies that require complex passwords and regular changes. Encourage the use of password managers to help individuals manage their credentials securely.
- Advanced Threat Protection (ATP) and Intrusion Detection Systems: Utilize advanced security tools like ATP and intrusion detection systems to monitor network traffic and identify malicious activities in real-time.
- Regular Security Audits and Penetration Testing: Conduct regular security audits and penetration testing to identify vulnerabilities in your systems and address them before attackers can exploit them.
The Legal Ramifications and Law Enforcement Response
The legal ramifications of such attacks are far-reaching. Victims face costly investigations, legal battles, and potential regulatory fines. The perpetrators face severe penalties, including hefty fines and prison sentences. However, tracking down and prosecuting these cybercriminals poses a significant challenge for law enforcement due to the often transnational nature of these crimes and the difficulty in tracing the attackers' digital footprints. Relevant laws and regulations, such as the GDPR and CCPA, significantly impact the legal landscape surrounding data breaches and the responsibilities of organizations to protect sensitive data.
Conclusion
This case demonstrates the devastating impact of sophisticated cyberattacks targeting executive Office 365 accounts. The methods employed, the significant financial losses incurred, and the complex legal ramifications highlight the critical need for robust cybersecurity practices. Protecting your executive Office 365 accounts requires a multifaceted approach that combines technological solutions with employee education and strong security policies. Failing to implement these measures leaves your organization vulnerable to similar attacks, potentially resulting in millions of dollars in losses. Strengthening Office 365 security is not an option; it's a necessity. To learn more about enhancing your Office 365 security and preventing millions in losses from Office 365 breaches, [link to relevant resources].

Featured Posts
-
 Miami Steakhouse John Travoltas Pulp Fiction Culinary Experience
Apr 24, 2025
Miami Steakhouse John Travoltas Pulp Fiction Culinary Experience
Apr 24, 2025 -
 Millions Made From Office365 Hacks Federal Investigation Into Executive Email Breaches
Apr 24, 2025
Millions Made From Office365 Hacks Federal Investigation Into Executive Email Breaches
Apr 24, 2025 -
 Cantor Fitzgerald In Talks For 3 Billion Crypto Spac With Tether And Soft Bank
Apr 24, 2025
Cantor Fitzgerald In Talks For 3 Billion Crypto Spac With Tether And Soft Bank
Apr 24, 2025 -
 Microsoft Activision Deal Ftcs Appeal And Its Implications
Apr 24, 2025
Microsoft Activision Deal Ftcs Appeal And Its Implications
Apr 24, 2025 -
 B And B April 9 Recap Steffy Blames Bill Finns Icu Status Liams Demand For Secrecy
Apr 24, 2025
B And B April 9 Recap Steffy Blames Bill Finns Icu Status Liams Demand For Secrecy
Apr 24, 2025
