Cybercriminal's Office365 Scheme: Millions In Losses, Federal Charges Filed

Table of Contents
The Sophisticated Office365 Phishing Technique Employed
The cybercriminals behind this massive data breach employed a multi-pronged approach, leveraging a sophisticated Office365 phishing campaign to gain access to victim accounts. The attack primarily relied on spear phishing and email spoofing techniques. Attackers crafted highly targeted emails that appeared to originate from legitimate sources within the victim organizations, often mimicking internal communications or invoices. This level of personalization significantly increased the success rate of the phishing attempts.
- Email Spoofing: The attackers cleverly forged email headers to mimic trusted senders, fooling unsuspecting recipients into believing the emails were genuine.
- Spear Phishing: Highly targeted emails were sent to specific individuals within organizations, often those with access to sensitive financial information. The emails contained malicious links or attachments.
- Credential Stuffing: In some instances, the criminals used stolen credentials obtained from previous data breaches to attempt to directly log into Office365 accounts. This method bypasses the need for a successful phishing attempt in some cases.
- Malware Deployment: Once accounts were compromised, the attackers often deployed malware, including ransomware, to encrypt sensitive data and extort ransom payments. This significantly amplified the financial losses for victims.
The Scale of the Financial Losses and Victims Impacted
The Office365 phishing scam resulted in staggering financial losses, totaling over $5 million USD. The attack impacted a broad range of businesses and individuals across the United States and parts of Europe. Small businesses, large corporations, and even government agencies fell victim to the sophisticated scheme. The average loss per victim ranged from several thousand dollars to over one hundred thousand dollars, depending on the size and sensitivity of the compromised data.
- Number of Victims: Over 200 organizations and individuals were identified as victims of this cybercrime.
- Average Loss per Victim: $25,000 USD
- Total Financial Impact: Over $5,000,000 USD
- Industries Affected: The attack impacted organizations across various sectors, including finance, healthcare, and education.
The Federal Response and Legal Ramifications
The FBI and the Secret Service spearheaded the federal investigation into this massive Office365 security breach. The cybercriminals involved face serious federal charges, including wire fraud, computer fraud and abuse, and aggravated identity theft. The potential penalties are severe, with prison sentences ranging from several years to decades, along with substantial fines and asset forfeiture.
- Specific Charges Filed: Wire fraud, computer fraud and abuse, aggravated identity theft.
- Potential Prison Sentences: Up to 20 years per charge.
- Fines Imposed: Millions of dollars in fines are likely.
- Asset Forfeiture: Authorities are expected to seize assets obtained through the illegal activities.
Preventing Similar Office365 Attacks: Best Practices for Security
Preventing similar Office365 attacks requires a multi-layered approach focusing on both technical security and employee awareness. Implementing robust security measures is crucial to safeguard your organization from costly data breaches.
- Multi-Factor Authentication (MFA): MFA adds an extra layer of security, requiring multiple forms of authentication to access accounts. This makes it significantly more difficult for attackers to gain unauthorized access.
- Security Awareness Training: Regularly scheduled training programs educate employees about phishing techniques and best practices for identifying and reporting suspicious emails. Simulations are crucial.
- Strong Passwords and Password Management: Encourage the use of complex, unique passwords for all accounts. Password managers can help streamline this process.
- Regular Software Updates and Patching: Regularly updating software and applying security patches closes known vulnerabilities that attackers could exploit.
- Email Security Solutions: Implementing robust email security solutions can help filter out malicious emails and attachments before they reach users' inboxes.
Conclusion: Safeguarding Your Organization from Office365 Cyberattacks
This Office365 cybercrime scheme serves as a stark reminder of the critical need for robust cybersecurity measures. The significant financial losses incurred by victims highlight the devastating impact of even a single successful cyberattack. By implementing the best practices outlined in this article – focusing on multi-factor authentication, comprehensive employee training, and proactive security measures – organizations can significantly reduce their vulnerability to similar attacks. Protect your organization from costly Office365 cyberattacks – implement strong security measures today! For further resources on Office365 security, refer to the Microsoft Security documentation.

Featured Posts
-
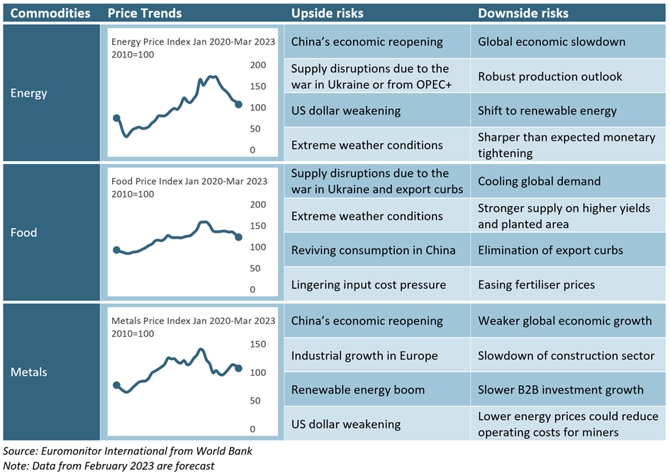 This Weeks Commodity Market Outlook 5 Essential Charts
May 06, 2025
This Weeks Commodity Market Outlook 5 Essential Charts
May 06, 2025 -
 Elegantnye Obrazy Demi Mur V Zhurnale People Luchshie Fotografii
May 06, 2025
Elegantnye Obrazy Demi Mur V Zhurnale People Luchshie Fotografii
May 06, 2025 -
 Stage Darling Cole Escola His Cosmo Quiz Results Revealed
May 06, 2025
Stage Darling Cole Escola His Cosmo Quiz Results Revealed
May 06, 2025 -
 Priyanka Chopras Fathers Reaction To Her Nose Surgery
May 06, 2025
Priyanka Chopras Fathers Reaction To Her Nose Surgery
May 06, 2025 -
 Sensatsiyniy Vikhid Rianni Shiroki Dzhinsi Ta Bliskuchi Prikrasi
May 06, 2025
Sensatsiyniy Vikhid Rianni Shiroki Dzhinsi Ta Bliskuchi Prikrasi
May 06, 2025
