Office 365 Breaches: Execs Targeted In Multi-Million Dollar Scheme

Table of Contents
The recent surge in sophisticated cyberattacks targeting high-ranking executives through Office 365 vulnerabilities has resulted in multi-million dollar losses for businesses worldwide. These aren't simple data breaches; they are meticulously planned schemes designed to exploit weaknesses in even the most robust security systems. This article delves into the methods employed in these breaches, the devastating consequences, and, crucially, the steps organizations can take to bolster their Office 365 security and protect themselves from similar attacks. Understanding the threat landscape of Office 365 security is the first step towards robust protection.
The Modus Operandi of Office 365 Breaches Targeting Executives
Cybercriminals are employing increasingly sophisticated techniques to breach Office 365 accounts, particularly those belonging to executives who often hold access to sensitive financial and strategic information. These attacks are rarely random; they are targeted and carefully planned.
Spear Phishing and Impersonation
Spear phishing remains a highly effective attack vector. Attackers craft highly personalized phishing emails designed to mimic legitimate communications from trusted sources. These emails might appear to be from the CEO, a board member, a major client, or even a trusted colleague.
- Highly personalized content: Emails often contain specific details gleaned from social media or public sources to increase credibility.
- Stolen credentials: Attackers often use stolen credentials obtained through previous breaches or dark web marketplaces to gain access to accounts.
- Social engineering tactics: These attacks leverage psychological manipulation to trick victims into clicking malicious links or revealing sensitive information.
- Example: An email appearing to be from the CEO requesting urgent wire transfer instructions to a seemingly legitimate account.
Once an account is compromised, attackers can use it as a springboard to infiltrate the internal network, accessing further sensitive data and potentially deploying ransomware.
Exploiting Zero-Day Vulnerabilities
Attackers are increasingly exploiting zero-day vulnerabilities – previously unknown flaws in software – to gain unauthorized access to Office 365 accounts. These vulnerabilities are particularly dangerous because they haven't been patched yet.
- Unpatched software: Outdated software is a prime target for exploitation.
- Prompt patching: Regularly updating software is crucial to mitigate this risk.
- Vulnerability scanners: Using vulnerability scanners can help identify potential weaknesses in your systems.
- Penetration testing: Regular penetration testing simulates real-world attacks to identify vulnerabilities before attackers can exploit them.
Compromised Third-Party Applications
Many organizations integrate third-party applications with their Office 365 environment. These applications, if not properly secured, can provide an entry point for attackers.
- Vulnerable apps: Poorly secured third-party apps can be exploited to gain unauthorized access.
- Vetting third-party apps: Thoroughly vet any third-party application before integration, ensuring it meets your security standards.
- Regular security audits: Conduct regular audits of third-party applications and their access privileges.
- Least privilege access: Grant only the minimum necessary access rights to all users and applications.
The Devastating Consequences of Office 365 Data Breaches
The consequences of a successful Office 365 data breach can be catastrophic, extending far beyond the immediate financial losses.
Financial Losses
Data breaches can lead to significant financial losses, including:
- Legal fees: Costs associated with legal investigations and potential lawsuits.
- Remediation costs: Expenses incurred in recovering from the breach, including data restoration and system repair.
- Reputational damage: The loss of customer trust and business can lead to significant revenue loss.
- Example: A major corporation suffering a multi-million dollar loss due to intellectual property theft and financial fraud following an Office 365 compromise.
Reputational Damage
The reputational damage caused by a data breach can be long-lasting and far-reaching.
- Loss of customer trust: Customers may lose faith in the organization’s ability to protect their data.
- Impact on investor confidence: Data breaches can negatively impact stock prices and investor confidence.
- Damaged brand image: A damaged reputation can make it difficult to attract new customers and partners.
Legal and Regulatory Compliance Issues
Organizations face significant legal and regulatory repercussions following a data breach.
- Fines and penalties: Organizations may face substantial fines for violating data privacy regulations.
- Lawsuits: Data breaches can result in costly lawsuits from affected individuals and businesses.
- Compliance issues: Failure to comply with regulations such as GDPR and CCPA can lead to severe penalties.
Protecting Your Organization from Office 365 Breaches
Protecting your organization from Office 365 breaches requires a proactive and multi-layered security approach.
Implementing Multi-Factor Authentication (MFA)
MFA adds an extra layer of security, making it significantly harder for attackers to gain access even if they have stolen passwords.
- Increased security: MFA significantly reduces the risk of unauthorized access.
- Various methods: Implement a combination of methods such as one-time codes, biometric authentication, and hardware tokens.
Enhancing Email Security
Investing in advanced email security solutions is crucial to protect against phishing attacks.
- Advanced threat protection: Employ solutions that detect and block malicious emails and attachments.
- Anti-phishing training: Regularly train employees to identify and report phishing attempts.
Regular Security Audits and Penetration Testing
Proactive security assessments are vital to identify and address vulnerabilities before they can be exploited.
- Vulnerability management: Implement a robust vulnerability management program to identify and remediate security flaws.
- Incident response planning: Develop a comprehensive incident response plan to effectively handle security incidents.
Keeping Software Updated
Maintaining updated software is critical to patching security vulnerabilities.
- Automated patching: Utilize automated patching solutions to ensure timely updates.
Conclusion:
Office 365 breaches targeting executives represent a significant and evolving threat, resulting in substantial financial and reputational damage. The sophistication of these attacks demands a multi-layered security approach that encompasses robust authentication, advanced threat protection, regular security assessments, and employee awareness training. Don't become the next victim of an Office 365 breach. Strengthen your organization's security posture today by implementing robust security measures and investing in advanced threat protection. Contact us to learn more about protecting your business from Office 365 vulnerabilities and mitigating the risks of executive targeting. Secure your Microsoft 365 environment and safeguard your business from costly cloud security breaches.

Featured Posts
-
 Is Dysprosium The Next Big Bottleneck For Electric Vehicle Production
Apr 29, 2025
Is Dysprosium The Next Big Bottleneck For Electric Vehicle Production
Apr 29, 2025 -
 Lionel Messi Inter Miami Games Full Mls Schedule Live Streams And Betting Odds
Apr 29, 2025
Lionel Messi Inter Miami Games Full Mls Schedule Live Streams And Betting Odds
Apr 29, 2025 -
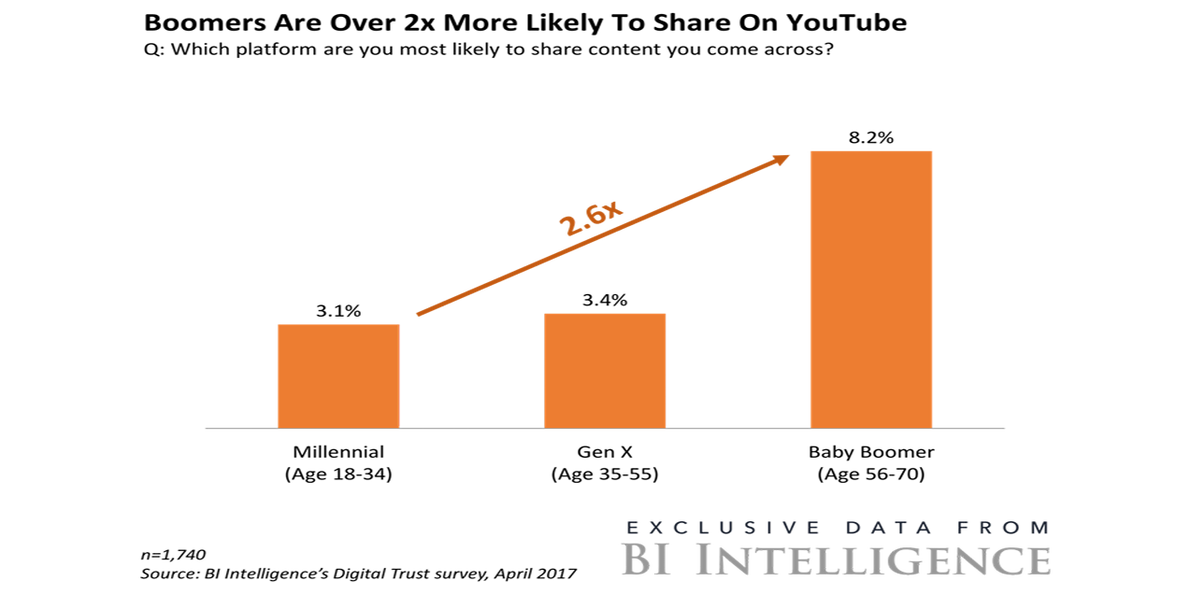 You Tubes Growing Popularity Among Older Viewers
Apr 29, 2025
You Tubes Growing Popularity Among Older Viewers
Apr 29, 2025 -
 Analyzing Tylor Megills Pitching How Hes Helping The Mets Win
Apr 29, 2025
Analyzing Tylor Megills Pitching How Hes Helping The Mets Win
Apr 29, 2025 -
 La Garantia De Gol De Alberto Ardila Olivares Un Analisis
Apr 29, 2025
La Garantia De Gol De Alberto Ardila Olivares Un Analisis
Apr 29, 2025
Latest Posts
-
 You Tubes Growing Popularity Among Older Viewers A Resurgence Of Classic Shows
Apr 29, 2025
You Tubes Growing Popularity Among Older Viewers A Resurgence Of Classic Shows
Apr 29, 2025 -
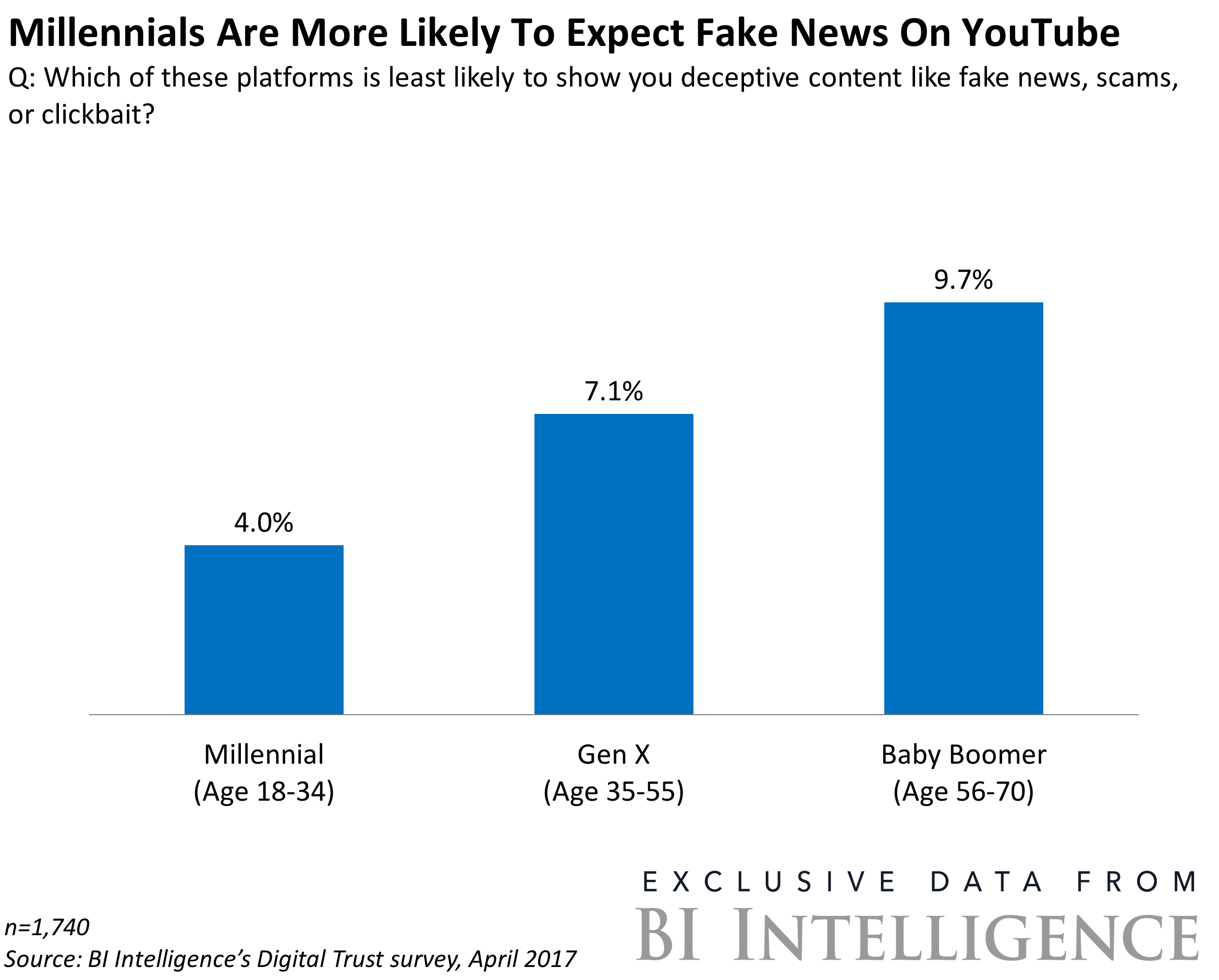 How Npr Explains You Tubes Expanding Older Adult User Base
Apr 29, 2025
How Npr Explains You Tubes Expanding Older Adult User Base
Apr 29, 2025 -
 Is You Tube Becoming A Senior Destination Npr Explores The Shift
Apr 29, 2025
Is You Tube Becoming A Senior Destination Npr Explores The Shift
Apr 29, 2025 -
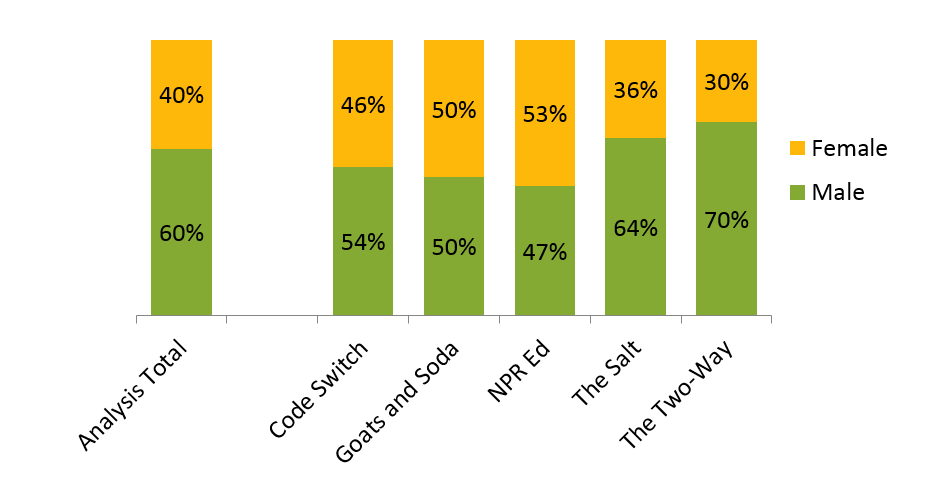 The Rise Of Older You Tube Users Data And Insights From Npr
Apr 29, 2025
The Rise Of Older You Tube Users Data And Insights From Npr
Apr 29, 2025 -
 Analyzing You Tubes Growth Among Older Demographics An Npr Perspective
Apr 29, 2025
Analyzing You Tubes Growth Among Older Demographics An Npr Perspective
Apr 29, 2025
