Understanding Data Transfers: Best Practices And Security
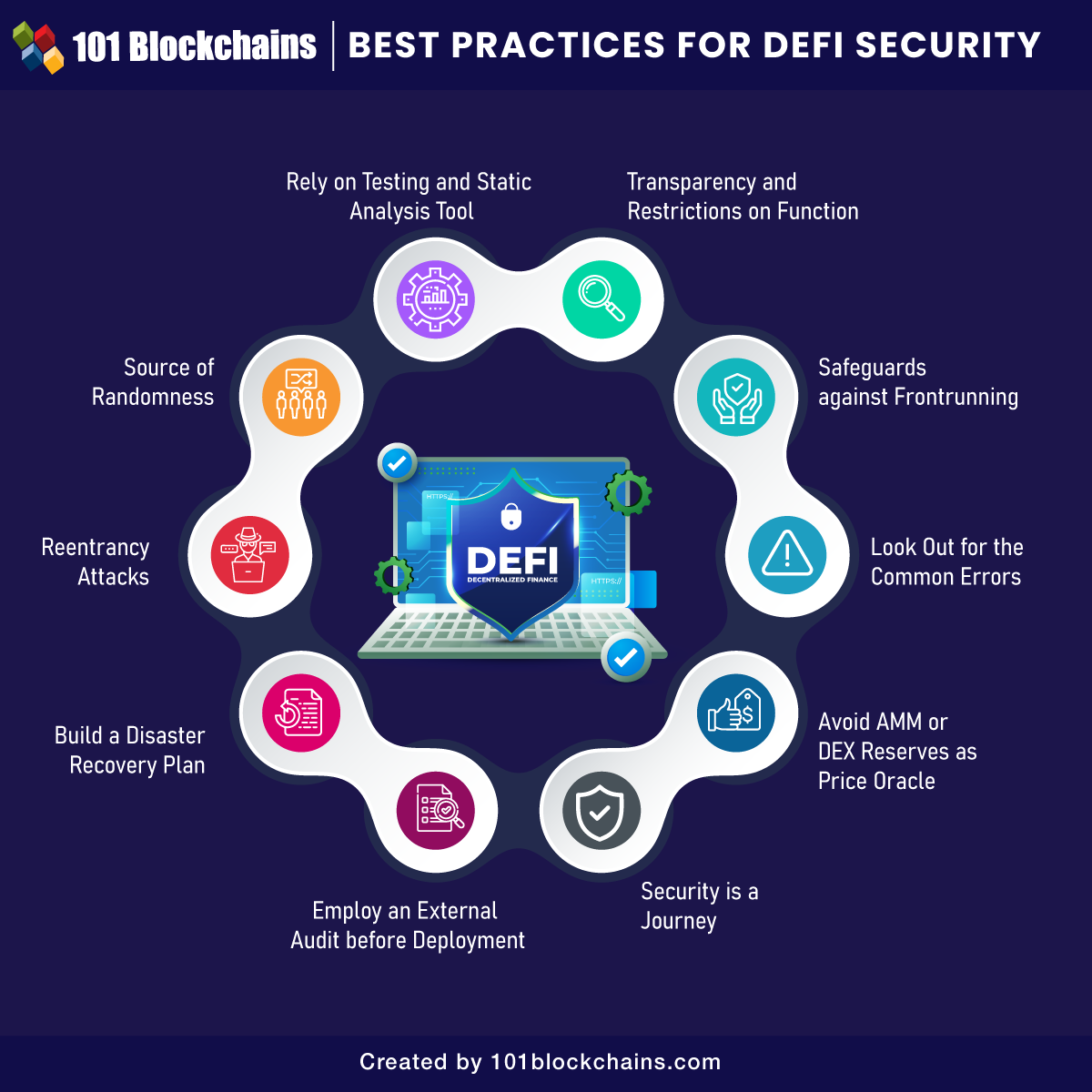
Table of Contents
Choosing the Right Data Transfer Method
Selecting the appropriate data transfer method is the first step towards ensuring secure and efficient data movement. The best choice depends on factors like data sensitivity, volume, and the technical expertise available. Here are some common methods:
File Transfer Protocol (FTP)
FTP is a widely used protocol for transferring files over a network. However, standard FTP transmits data in plain text, making it vulnerable to interception.
- Suitable for: Smaller files and less sensitive data.
- Security Concerns: Lacks inherent security; easily susceptible to man-in-the-middle attacks.
- Enhanced Security: Requires using Secure FTP (SFTP) or FTPS (FTP over SSL/TLS) which encrypts the data during transit.
- Limitations: Can be slow and less scalable for large datasets.
Secure Copy Protocol (SCP)
SCP is a more secure alternative to FTP, utilizing SSH (Secure Shell) for encryption and authentication.
- Ideal for: Transferring sensitive data between servers.
- Security Advantages: Offers strong authentication and encryption during the entire transfer process.
- Technical Expertise: Requires some familiarity with command-line interfaces.
- Scalability: Relatively scalable for moderate data volumes.
Secure Shell (SSH)
SSH is a powerful tool providing secure remote access to servers and enabling secure file transfers.
- Versatility: Manages servers and securely transfers files.
- Security: Offers robust encryption and authentication.
- Command-Line Interface: Requires familiarity with command-line interactions.
- File Transfer: Uses the
scpcommand orsftpfor file transfer capabilities.
Cloud-Based Solutions
Cloud storage services like Dropbox, Google Drive, and OneDrive offer convenient and user-friendly data transfer options.
- Collaboration: Excellent for file sharing and collaboration.
- Security Dependence: Security relies on the provider's infrastructure and your user settings. Always review their security policies and practices.
- Data Sovereignty: Consider data location and compliance with regulations like GDPR.
- Scalability: Typically offer good scalability for various data sizes.
Data Transfer via APIs
APIs (Application Programming Interfaces) are ideal for automated and large-scale data transfers between applications and systems.
- Automation: Supports automated, scheduled transfers.
- Scalability: Highly scalable for massive datasets.
- Programming Knowledge: Requires programming skills and integration expertise.
- Security: Requires careful implementation of authentication (e.g., OAuth 2.0, API keys) and authorization mechanisms.
Implementing Robust Security Measures for Data Transfers
Protecting data during transfer requires a multi-layered security approach.
Encryption
Encryption is paramount to protect data both in transit and at rest.
- Algorithms: Use strong encryption algorithms like AES-256.
- End-to-End Encryption: Implement whenever possible to protect data from unauthorized access at any point.
- Key Management: Regularly rotate and update encryption keys and certificates.
- Protocols: Choose protocols that support encryption (e.g., SFTP, FTPS, HTTPS).
Authentication and Authorization
Verify the identity of users and systems accessing data.
- Multi-Factor Authentication (MFA): Employ MFA for enhanced security.
- Access Control Lists (ACLs): Implement fine-grained access control to restrict access based on roles and permissions.
- Regular Reviews: Periodically review and update user permissions to minimize risk.
- Principle of Least Privilege: Grant only the necessary permissions to users and systems.
Data Loss Prevention (DLP)
Prevent accidental or malicious data loss.
- DLP Tools: Utilize DLP tools to monitor and control data transfers.
- Data Backup and Recovery: Establish robust backup and disaster recovery procedures.
- Employee Training: Educate employees on data security best practices.
- Incident Response Plan: Develop a plan to handle data breaches and other security incidents.
Regular Security Audits and Penetration Testing
Proactively identify and address vulnerabilities.
- Regular Assessments: Conduct regular security audits to identify weaknesses.
- Penetration Testing: Simulate real-world attacks to identify exploitable vulnerabilities.
- Vulnerability Management: Address identified vulnerabilities promptly and effectively.
- Compliance: Ensure adherence to relevant industry regulations and standards (e.g., HIPAA, PCI DSS).
Best Practices for Secure Data Transfers
Beyond specific methods and security measures, these practices are crucial:
- Software Updates: Keep software and security protocols updated.
- Strong Passwords: Use strong, unique passwords for all accounts.
- VPNs: Employ VPNs for secure communication over public networks.
- Activity Monitoring: Monitor data transfer activity for suspicious behavior.
- Data Security Policy: Implement a comprehensive data security policy.
- Security Awareness Training: Regularly train employees on data security best practices.
Conclusion
Understanding data transfer methods and implementing robust security measures is vital for data integrity and confidentiality. By carefully choosing secure protocols like SFTP and SCP, implementing encryption, and utilizing multi-factor authentication, you can significantly reduce the risk of data breaches. Prioritizing secure data transfer practices isn't just a best practice; it's a necessity. Invest time in learning more about secure data transfer methods and implement a robust strategy to safeguard your valuable data. Improve your data transfer security today!

Featured Posts
-
 Andor Season 2 Release Date Trailer And Everything We Know So Far
May 08, 2025
Andor Season 2 Release Date Trailer And Everything We Know So Far
May 08, 2025 -
 Superiorite Geometrique Des Corneilles Sur Les Babouins Etude Fascinante
May 08, 2025
Superiorite Geometrique Des Corneilles Sur Les Babouins Etude Fascinante
May 08, 2025 -
 Bitcoin Price Rebound Analyzing The Potential For Further Growth
May 08, 2025
Bitcoin Price Rebound Analyzing The Potential For Further Growth
May 08, 2025 -
 Am I Due A Universal Credit Refund From The Dwp
May 08, 2025
Am I Due A Universal Credit Refund From The Dwp
May 08, 2025 -
 Kyren Paris Late Homer Powers Angels To Rain Soaked Victory Over White Sox
May 08, 2025
Kyren Paris Late Homer Powers Angels To Rain Soaked Victory Over White Sox
May 08, 2025
Latest Posts
-
 Nepogoda V Yaroslavskoy Oblasti Gotovnost K Snegopadam
May 09, 2025
Nepogoda V Yaroslavskoy Oblasti Gotovnost K Snegopadam
May 09, 2025 -
 Imalaia Elaxista Xionia Se 23etia Anisyxia Gia To Mellon
May 09, 2025
Imalaia Elaxista Xionia Se 23etia Anisyxia Gia To Mellon
May 09, 2025 -
 Silniy Snegopad Ostavil 45 000 Chelovek V Sverdlovskoy Oblasti Bez Sveta
May 09, 2025
Silniy Snegopad Ostavil 45 000 Chelovek V Sverdlovskoy Oblasti Bez Sveta
May 09, 2025 -
 Yaroslavskaya Oblast Preduprezhdenie O Snegopadakh I Meteli
May 09, 2025
Yaroslavskaya Oblast Preduprezhdenie O Snegopadakh I Meteli
May 09, 2025 -
 Pogoda Perm I Permskiy Kray Konets Aprelya 2025 Snegopady Pokholodanie
May 09, 2025
Pogoda Perm I Permskiy Kray Konets Aprelya 2025 Snegopady Pokholodanie
May 09, 2025
