Office365 Breaches Net Millions For Hacker Targeting Executives
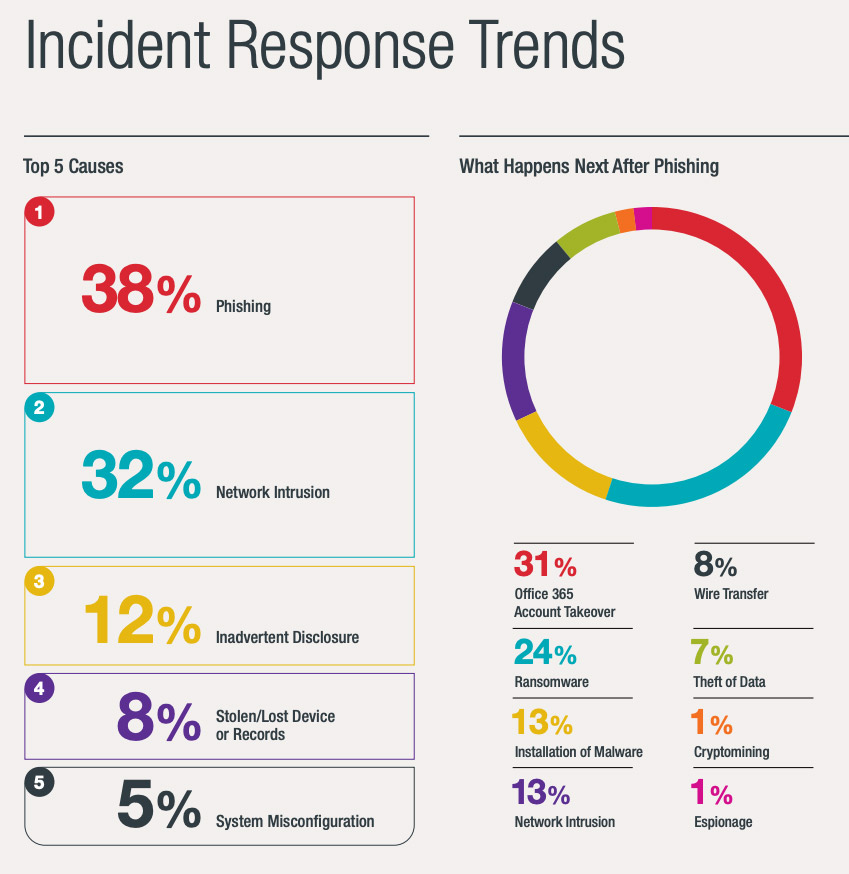
Table of Contents
Sophisticated Phishing Attacks Targeting Executives
Executives are prime targets for cybercriminals due to their access to sensitive information and critical decision-making power. A successful breach involving an executive can unlock vast resources and potentially cripple an entire organization. Furthermore, executives are often less familiar with the latest cybersecurity threats and may be more susceptible to social engineering tactics.
Why Executives are Prime Targets:
-
High-Value Information: Executives possess access to sensitive company data, including financial records, strategic plans, and intellectual property, making them lucrative targets for data theft and corporate espionage.
-
Decision-Making Power: Compromising an executive account can allow attackers to manipulate business decisions, potentially leading to financial fraud or the dissemination of misinformation.
-
Insider Threat Potential: A compromised executive account can be leveraged to gain access to internal systems, creating an insider threat and exacerbating the damage.
-
Spear phishing campaigns using personalized emails and attachments designed to mimic legitimate communications are a common tactic. These emails often exploit current events or company news to increase their credibility.
-
Exploitation of known vulnerabilities in Office365 applications, such as outdated software or unpatched security flaws, provide an easy entry point for attackers.
-
Social engineering tactics, including building rapport and creating a sense of urgency, are used to manipulate executives into revealing sensitive information or clicking malicious links.
-
Successful attacks have resulted in significant financial losses, reputational damage, and legal repercussions for numerous organizations worldwide.
The Financial Impact of Office365 Breaches
The financial consequences of Office365 breaches targeting executives are substantial and far-reaching. The costs extend beyond the immediate expenses of data recovery and remediation.
Direct Costs:
- Data recovery and remediation: The process of restoring compromised systems and data can be incredibly expensive, requiring specialized expertise and significant time investment.
- Legal fees: Organizations often face costly legal battles, including lawsuits from affected parties and regulatory investigations.
- Regulatory fines: Non-compliance with data protection regulations can lead to substantial fines, particularly under regulations like GDPR and CCPA.
- Notification costs: Informing affected individuals and stakeholders about the breach can involve significant costs associated with communication and credit monitoring services.
Indirect Costs:
-
Reputational damage: A successful breach can severely damage an organization's reputation, eroding trust among customers, investors, and partners.
-
Loss of investor confidence: Negative publicity surrounding a data breach can lead to a decline in stock value and reduced investor confidence.
-
Decreased productivity: The disruption caused by a breach can impact productivity, requiring employees to spend time on recovery efforts instead of their core responsibilities.
-
Statistics indicate that the average cost of a data breach is increasing annually, with the cost of breaches targeting executives significantly higher.
-
Numerous high-profile examples demonstrate the devastating financial impact of Office365 breaches, resulting in losses exceeding millions of dollars for affected companies.
-
Cybersecurity insurance can help mitigate some of the financial risks, but comprehensive risk assessment and proactive security measures are crucial for reducing the likelihood and severity of breaches.
Best Practices for Preventing Office365 Breaches
Implementing robust security measures is essential for preventing Office365 breaches and protecting your organization from the devastating financial and reputational consequences.
Multi-Factor Authentication (MFA):
MFA is a crucial security layer that adds an extra level of protection beyond passwords. By requiring multiple forms of authentication, MFA significantly reduces the risk of unauthorized access, even if passwords are compromised.
Employee Training and Awareness:
Regular security awareness training is essential to educate employees, particularly executives, about the latest phishing techniques and social engineering tactics. Training should cover topics like recognizing phishing emails, avoiding malicious links, and practicing safe browsing habits.
Regular Security Audits and Updates:
Proactive security measures, such as regular security audits and software updates, are critical for identifying and addressing vulnerabilities before attackers can exploit them. This includes patching known security flaws in Office365 applications and other software.
- Implement strong passwords and password managers: Enforce strong password policies and encourage the use of password managers to generate and securely store complex passwords.
- Regular software updates and patching: Stay up-to-date with the latest security patches and updates for all software applications, including Office365.
- Utilize advanced threat protection tools: Implement advanced threat protection solutions to detect and prevent malicious activities, including phishing attacks and malware.
- Implement Data Loss Prevention (DLP) strategies: Implement DLP policies to prevent sensitive data from leaving the organization's network.
- Develop and regularly test incident response plans: Having a well-defined incident response plan will help to minimize the impact of a successful breach.
Conclusion
Office365 breaches targeting executives pose a significant threat to organizations, resulting in substantial financial losses and reputational damage. Sophisticated phishing attacks, coupled with the exploitation of vulnerabilities, make strong security measures paramount. By implementing multi-factor authentication, conducting regular employee training, and performing routine security audits, organizations can significantly reduce their risk of experiencing these costly and damaging breaches. Proactive cybersecurity strategies, including the use of advanced threat protection tools and robust incident response plans, are crucial for preventing Office365 data breaches and strengthening Office365 security overall. Don't wait for a costly breach to occur – take action today to protect your executives and your organization from cyberattacks. Learn more about strengthening your Office365 security by visiting [link to relevant resource/service].

Featured Posts
-
 Us Economic Trends And Their Influence On Elon Musks Fortune
May 09, 2025
Us Economic Trends And Their Influence On Elon Musks Fortune
May 09, 2025 -
 Formula 1s Next Star Colapinto Emerges As Strong Contender
May 09, 2025
Formula 1s Next Star Colapinto Emerges As Strong Contender
May 09, 2025 -
 The Feds Rationale Why Rate Cuts Remain Unlikely
May 09, 2025
The Feds Rationale Why Rate Cuts Remain Unlikely
May 09, 2025 -
 Elon Musks Net Worth A 100 Day Analysis Under Trumps Presidency
May 09, 2025
Elon Musks Net Worth A 100 Day Analysis Under Trumps Presidency
May 09, 2025 -
 Bayern Munich Vs Fc St Pauli A Comprehensive Match Preview
May 09, 2025
Bayern Munich Vs Fc St Pauli A Comprehensive Match Preview
May 09, 2025
Latest Posts
-
 Reaktsiya Na Slova Kinga Mask Ta Tramp Zradniki Za Slovami Pismennika
May 09, 2025
Reaktsiya Na Slova Kinga Mask Ta Tramp Zradniki Za Slovami Pismennika
May 09, 2025 -
 Vozvraschenie Stivena Kinga V X Oskorblenie Ilona Maska
May 09, 2025
Vozvraschenie Stivena Kinga V X Oskorblenie Ilona Maska
May 09, 2025 -
 King Pro Maska Ta Trampa Zrada Chi Politichna Zayava
May 09, 2025
King Pro Maska Ta Trampa Zrada Chi Politichna Zayava
May 09, 2025 -
 King Zvinuvachuye Maska Ta Trampa V Zradi Detali Zayavi Pismennika
May 09, 2025
King Zvinuvachuye Maska Ta Trampa V Zradi Detali Zayavi Pismennika
May 09, 2025 -
 Stephen King 5 Famous Feuds You Might Not Know About
May 09, 2025
Stephen King 5 Famous Feuds You Might Not Know About
May 09, 2025
