Federal Investigation: Hacker Makes Millions From Executive Office365 Accounts

Table of Contents
The Scope of the Office 365 Breach
This data breach represents a significant cyberattack with far-reaching consequences. The scale of the financial loss and the number of compromised accounts are staggering, emphasizing the gravity of the situation.
- Number of compromised accounts: While the exact number remains undisclosed during the ongoing federal investigation, sources suggest potentially hundreds of executive-level accounts across various organizations were affected.
- Types of organizations targeted: The breach impacted a diverse range of organizations, including Fortune 500 companies, government agencies, and large financial institutions. The hacker specifically targeted executive accounts, likely for access to sensitive financial data and privileged information.
- Financial losses: Estimates place the total financial loss in the tens of millions of dollars. The exact figure is still under investigation, as the full extent of the data breach continues to unfold. Losses include direct theft of funds, costs associated with remediation efforts, and potential reputational damage.
- Types of data accessed: The stolen data encompassed a wide array of sensitive information, including financial records, strategic plans, intellectual property, employee personal information, and confidential client data. This broad access poses significant risks across multiple areas.
The sheer scale of this breach underscores the vulnerability of even the most sophisticated organizations to well-executed cyberattacks. The methods used to estimate the losses involved forensic analysis of compromised systems, financial transaction records, and interviews with affected organizations. The ongoing investigation aims to pinpoint the full extent of the damage.
The Hacker's Methods and Tactics
The sophistication of the hacking techniques employed in this breach is alarming. The hacker demonstrated a high level of technical expertise and knowledge of Office 365 vulnerabilities.
- Initial access vector: The investigation suggests the hacker initially gained access through a combination of sophisticated phishing emails targeting executives and exploiting known, but unpatched, vulnerabilities in older versions of Office 365 software.
- Techniques used to maintain access: Once inside, the hacker used malware to maintain persistent access to the compromised accounts, employing techniques such as credential theft and privilege escalation to move laterally within the network.
- Methods of exfiltrating data: Data exfiltration involved the use of encrypted channels and cloud storage services, often located outside of the targeted organization's jurisdiction, making it difficult for law enforcement to trace.
- Money laundering methods: Initial reports indicate the stolen funds were laundered through a complex network of offshore accounts and cryptocurrency transactions, making tracking the money a significant challenge for investigators.
The hacker's methods highlight the need for organizations to adopt a multi-layered security approach, encompassing proactive threat detection and response strategies. The techniques used to circumvent security protocols represent a significant challenge to existing cyber defense strategies.
The Federal Investigation and Legal Ramifications
The federal investigation into this Office 365 hack is a significant undertaking, involving multiple agencies committed to bringing the perpetrator to justice.
- Agencies involved in the investigation: The FBI, Secret Service, and potentially other federal agencies are actively involved in the investigation, collaborating to trace the hacker's activities and recover stolen funds.
- Current status of the investigation: The investigation is ongoing, with law enforcement actively pursuing leads and working to identify and apprehend the individual or group responsible for the breach. At the time of writing, no arrests have been publicly announced.
- Potential charges against the hacker: The hacker faces a range of serious federal charges, including wire fraud, identity theft, computer fraud and abuse, and potentially conspiracy charges depending on the number of individuals involved.
- Potential penalties: The penalties for these crimes are severe, including lengthy prison sentences, substantial fines, and mandatory restitution to the victims.
The ongoing investigation's outcome will have significant implications for future cybersecurity legislation and enforcement. It serves as a stark reminder of the serious consequences of cybercrime.
Protecting Your Organization from Similar Office 365 Attacks
Organizations must proactively enhance their Office 365 security to mitigate the risk of similar attacks. Implementing a layered security approach is crucial.
- Implement multi-factor authentication (MFA): MFA adds an extra layer of security, making it significantly harder for hackers to access accounts even if they obtain usernames and passwords.
- Regularly update software and security patches: Keeping software updated patches vulnerabilities that hackers exploit. Regular patching is critical for all systems, especially Office 365 applications.
- Conduct employee security awareness training: Educating employees about phishing scams, malware, and other social engineering tactics is crucial in preventing initial access.
- Implement robust intrusion detection and prevention systems: Employing sophisticated systems can help identify and block malicious activity before it causes significant damage.
- Regularly back up important data: Regularly backing up data provides a safety net in case of a data breach. This minimizes the impact of the incident.
By adopting these best practices, organizations can significantly strengthen their Office 365 security posture and proactively prevent costly data breaches. A layered security approach is crucial, combining technological safeguards with employee education and awareness.
Conclusion
The federal investigation into the hacking of executive Office 365 accounts highlights the escalating threat of sophisticated cyberattacks targeting high-value data and finances. The breach's scale underscores the urgent need for enhanced security measures, including the adoption of best practices outlined above. This incident serves as a critical wake-up call for all organizations reliant on cloud-based services like Office 365.
Call to Action: Don't become the next victim. Protect your organization's Office 365 accounts and data by implementing robust cybersecurity measures today. Learn more about securing your Office 365 environment and preventing costly Office 365 data breaches to safeguard your organization's future.

Featured Posts
-
 Ramiro Helmeyer Dedication To Fc Barcelonas Glory
Apr 27, 2025
Ramiro Helmeyer Dedication To Fc Barcelonas Glory
Apr 27, 2025 -
 Thueringen Artenvielfalt Von Eidechsen Und Molchen Im Neuen Atlas
Apr 27, 2025
Thueringen Artenvielfalt Von Eidechsen Und Molchen Im Neuen Atlas
Apr 27, 2025 -
 Ariana Grandes New Hair And Tattoos Professional Styling And Artistry
Apr 27, 2025
Ariana Grandes New Hair And Tattoos Professional Styling And Artistry
Apr 27, 2025 -
 Ev Mandates Face Renewed Opposition From Car Dealerships
Apr 27, 2025
Ev Mandates Face Renewed Opposition From Car Dealerships
Apr 27, 2025 -
 Professional Help For Hair And Tattoo Transformations Inspired By Ariana Grande
Apr 27, 2025
Professional Help For Hair And Tattoo Transformations Inspired By Ariana Grande
Apr 27, 2025
Latest Posts
-
 The U S Dollars First 100 Days A Historical Comparison
Apr 28, 2025
The U S Dollars First 100 Days A Historical Comparison
Apr 28, 2025 -
 U S Dollars Troubled Start Parallels To The Nixon Presidency
Apr 28, 2025
U S Dollars Troubled Start Parallels To The Nixon Presidency
Apr 28, 2025 -
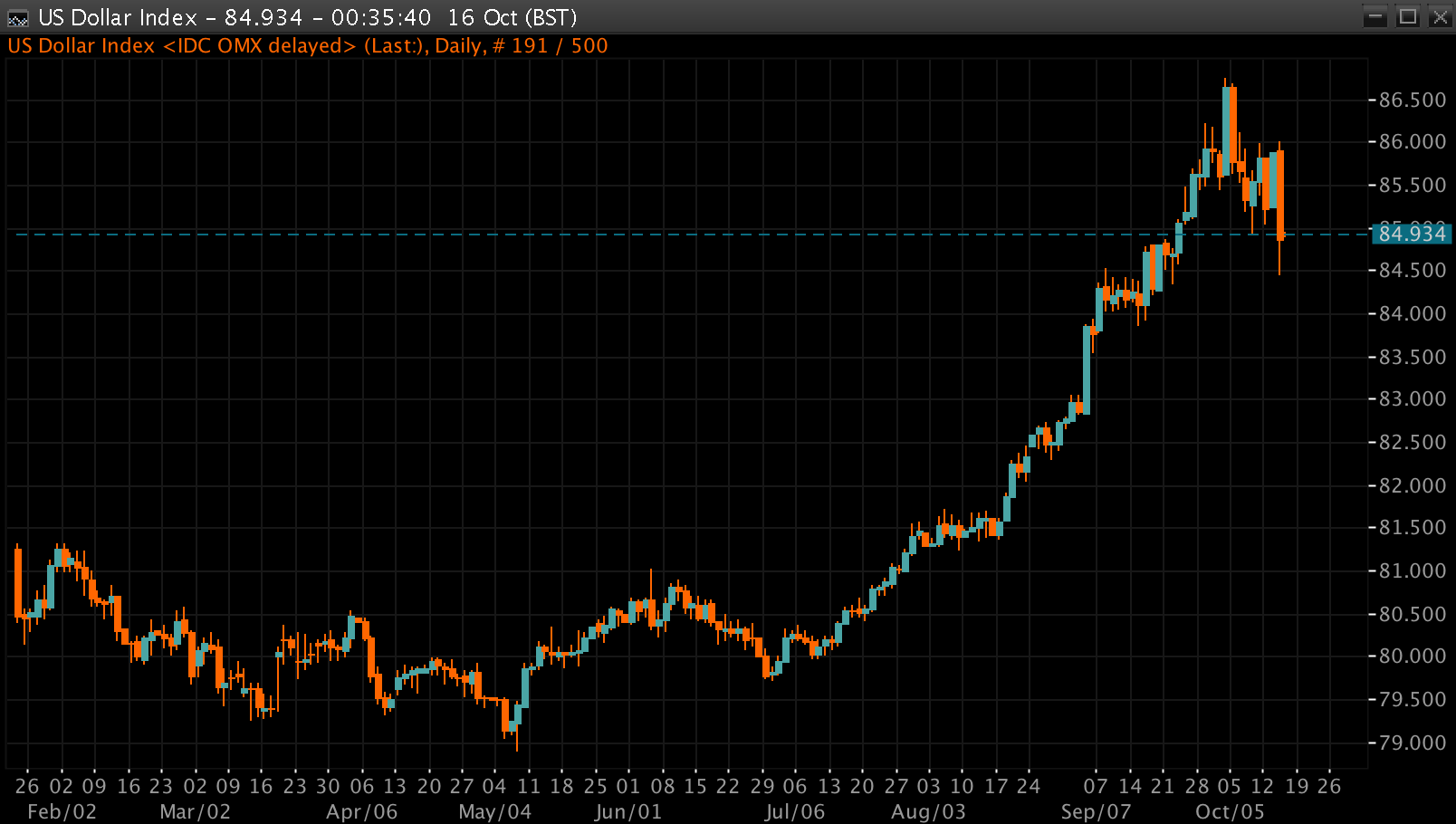 Nixons Shadow A Look At The Current U S Dollars Performance
Apr 28, 2025
Nixons Shadow A Look At The Current U S Dollars Performance
Apr 28, 2025 -
 U S Dollar Weak Start To Presidency Mirrors Nixon Era
Apr 28, 2025
U S Dollar Weak Start To Presidency Mirrors Nixon Era
Apr 28, 2025 -
 Yukon Legislature Mine Managers Testimony Sparks Contempt Threat
Apr 28, 2025
Yukon Legislature Mine Managers Testimony Sparks Contempt Threat
Apr 28, 2025
