Office365 Executive Inboxes Targeted: Millions Stolen In Cybercrime
Table of Contents
Methods Used in Office365 Executive Inbox Attacks
Cybercriminals employ a range of increasingly sophisticated techniques to gain access to Office365 executive inboxes. Understanding these methods is the first step towards effective prevention.
Spear Phishing and Whaling
Spear phishing and whaling are highly targeted phishing attacks designed to deceive executives. Unlike generic phishing emails, these attacks are meticulously crafted, using personalized information gleaned from social media, company websites, and other publicly available sources. These personalized touches make them far more believable and likely to bypass traditional security filters.
- Personalized emails: Attackers craft emails that appear to be from trusted sources, often mimicking the style and tone of known contacts or business partners.
- Urgency and emotional manipulation: Emails often create a sense of urgency or leverage emotional triggers to pressure recipients into acting quickly without thinking critically.
- Malicious links and attachments: Clicking on malicious links can download malware or redirect users to fake login pages designed to steal credentials. Opening infected attachments can similarly compromise the system.
- Social engineering: Attackers often use social engineering techniques, manipulating the recipient's psychology to elicit a desired response, such as revealing sensitive information or clicking a malicious link. For example, an email might pretend to be from the CEO requesting urgent financial information.
Credential Stuffing and Brute-Force Attacks
Attackers often leverage stolen credentials obtained from previous data breaches. This technique, known as credential stuffing, involves attempting to use stolen usernames and passwords against a wide range of services, including Office365. If an executive reuses passwords across multiple platforms, this technique can easily succeed.
- Stolen credentials: Data breaches on other websites often expose usernames and passwords which are then used against Office365 accounts.
- Brute-force attacks: These attacks involve systematically trying various password combinations until the correct one is found. Weak or easily guessable passwords are particularly vulnerable.
- Password reuse: The practice of reusing the same password across multiple accounts significantly increases vulnerability to credential stuffing.
Exploiting Vulnerabilities in Third-Party Apps
Many organizations integrate third-party applications with Office365 to enhance productivity. However, vulnerabilities in these apps can provide an entry point for attackers.
- Unpatched applications: Out-of-date third-party apps with known security vulnerabilities can be exploited.
- Weak security practices: Poor security practices in the development or maintenance of third-party apps can create opportunities for attackers.
- Lack of regular audits: Failure to regularly audit integrated applications for vulnerabilities increases the risk of compromise.
The Impact of Compromised Office365 Executive Inboxes
The consequences of a successful Office365 executive inbox compromise can be severe and far-reaching, impacting various aspects of the organization.
Financial Losses
The financial impact of a compromised executive inbox can be devastating.
- Fraudulent transactions: Attackers can initiate fraudulent wire transfers, payments, and other financial transactions.
- Data breaches: Stolen data can lead to significant financial losses due to regulatory fines, legal fees, and reputational damage.
- Business disruption: Compromised accounts can lead to significant business disruption and lost productivity.
Reputational Damage
A security breach can severely damage an organization's reputation and erode trust among customers, investors, and partners.
- Loss of customer trust: News of a data breach can lead to customers losing faith in the organization's ability to protect their data.
- Investor concerns: Investors may lose confidence, impacting the organization's stock price and fundraising ability.
- Negative publicity: Negative media coverage can further damage reputation and erode public trust.
Legal and Regulatory Consequences
Organizations facing a data breach due to an Office365 executive inbox compromise can face significant legal and regulatory repercussions.
- Data privacy regulations (GDPR, CCPA): Non-compliance with regulations like GDPR and CCPA can result in substantial fines and penalties.
- Lawsuits: Affected individuals and organizations may file lawsuits seeking compensation for damages.
Protecting Your Office365 Executive Inboxes
Protecting your organization from Office365 executive inbox compromise requires a multi-layered approach.
Multi-Factor Authentication (MFA)
Implementing MFA is crucial for preventing unauthorized access, even if credentials are compromised.
- OTP (One-Time Passwords): Requires a code from a mobile app or SMS message in addition to a password.
- Biometrics: Utilizes fingerprint, facial recognition, or other biometric methods for authentication.
Advanced Threat Protection (ATP)
Microsoft's ATP offers advanced protection against phishing attacks and malware.
- Anti-phishing: Detects and blocks malicious emails designed to trick users into revealing sensitive information.
- Anti-malware: Scans attachments and links for malicious code, preventing infections.
Security Awareness Training
Regular security awareness training is essential to educate executives and employees on best practices.
- Phishing simulations: Regular simulations help users identify and report suspicious emails.
- Cybersecurity best practices: Training should cover topics such as strong password creation, safe browsing habits, and recognizing phishing attempts.
Regular Security Audits and Penetration Testing
Regular security assessments help identify and address vulnerabilities before they can be exploited.
- Vulnerability scans: Identify security weaknesses in systems and applications.
- Penetration testing: Simulates real-world attacks to test the effectiveness of security measures.
Strong Password Policies and Management
Implementing a strong password policy and using a password manager is critical.
- Password manager: Helps executives manage strong, unique passwords for all their accounts.
- Strong password policy: Requires passwords to meet certain criteria, such as length, complexity, and regular changes.
Conclusion: Safeguarding Your Organization from Office365 Executive Inbox Compromise
The threat of Office365 executive inbox compromise is real and poses significant risks to organizations. The methods used are sophisticated, and the consequences can be devastating, leading to substantial financial losses, reputational damage, and legal repercussions. By implementing the preventative measures outlined above—including robust MFA, ATP, comprehensive security awareness training, regular security audits, and strong password policies—organizations can significantly reduce their vulnerability and protect their valuable assets. Don't become another statistic – take immediate steps to secure your Office365 executive inboxes and protect your organization from the devastating consequences of a successful attack. For more information, consult Microsoft's security documentation and resources.

Featured Posts
-
 Dodger Mookie Betts Misses Freeway Series Opener Due To Illness
May 08, 2025
Dodger Mookie Betts Misses Freeway Series Opener Due To Illness
May 08, 2025 -
 Arsenal Vs Psg Gary Nevilles Bold Prediction
May 08, 2025
Arsenal Vs Psg Gary Nevilles Bold Prediction
May 08, 2025 -
 Arsenals Dembele Concerns Latest Injury Update And Its Impact
May 08, 2025
Arsenals Dembele Concerns Latest Injury Update And Its Impact
May 08, 2025 -
 Hargreaves Predicts Winner Arsenal Or Psg In Champions League Final
May 08, 2025
Hargreaves Predicts Winner Arsenal Or Psg In Champions League Final
May 08, 2025 -
 March 2024 Play Station Plus Premium And Extra Game Catalog
May 08, 2025
March 2024 Play Station Plus Premium And Extra Game Catalog
May 08, 2025
Latest Posts
-
 Black Rock Etf Billionaire Investments Fuel 110 Growth Prediction For 2025
May 08, 2025
Black Rock Etf Billionaire Investments Fuel 110 Growth Prediction For 2025
May 08, 2025 -
 110 Gain Potential Why Billionaires Are Investing In This Black Rock Etf
May 08, 2025
110 Gain Potential Why Billionaires Are Investing In This Black Rock Etf
May 08, 2025 -
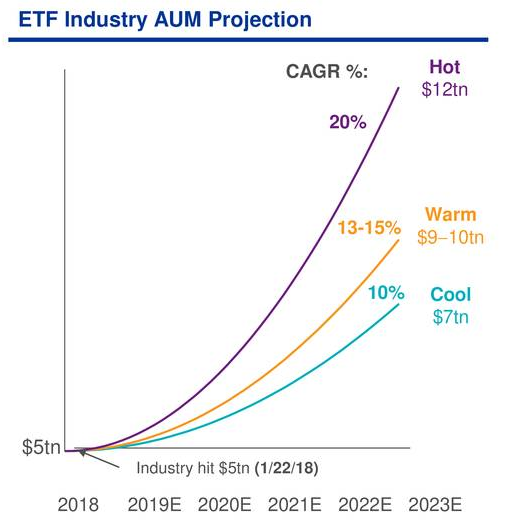 110 Growth Potential Why Billionaires Are Investing In This Black Rock Etf
May 08, 2025
110 Growth Potential Why Billionaires Are Investing In This Black Rock Etf
May 08, 2025 -
 Wall Streets Next Big Thing Billionaire Backed Etf Poised For 110 Growth
May 08, 2025
Wall Streets Next Big Thing Billionaire Backed Etf Poised For 110 Growth
May 08, 2025 -
 Wall Streets Bullish Prediction This Black Rock Etf Could Surge 110 In 2025
May 08, 2025
Wall Streets Bullish Prediction This Black Rock Etf Could Surge 110 In 2025
May 08, 2025
